PUBLISHER: Global Market Insights Inc. | PRODUCT CODE: 1913292

PUBLISHER: Global Market Insights Inc. | PRODUCT CODE: 1913292
Secure Access Service Edge Market Opportunity, Growth Drivers, Industry Trend Analysis, and Forecast 2026 - 2035
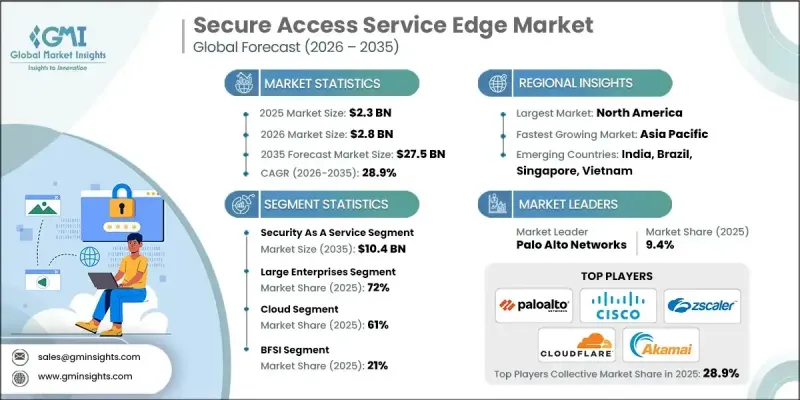
The Global Secure Access Service Edge Market was valued at USD 2.3 billion in 2025 and is estimated to grow at a CAGR of 28.9% to reach USD 27.5 billion by 2035.
Organizations across industries are accelerating the shift toward cloud-delivered applications, which is redefining how enterprise networks and security are designed. As reliance on cloud-hosted software grows, companies are moving away from legacy perimeter-based defenses and adopting cloud-centric SASE architectures that deliver unified connectivity and security. Enterprises increasingly require consistent protection and optimized performance for users and devices regardless of location. This demand is driving adoption of centrally managed, policy-driven SASE platforms that support secure global access while maintaining operational flexibility. Distributed workforces, cloud migration, and the need for scalable infrastructure are reshaping enterprise security strategies. Organizations are prioritizing simplified management, stronger identity-based controls, and integrated networking and security models to support evolving business operations and long-term digital transformation goals.
| Market Scope | |
|---|---|
| Start Year | 2025 |
| Forecast Year | 2026-2035 |
| Start Value | $2.3 Billion |
| Forecast Value | $27.5 Billion |
| CAGR | 28.9% |
The growing use of fragmented security tools has increased operational complexity and cost, prompting organizations to consolidate networking and security into integrated platforms. Unified SASE deployments allow enterprises to modernize IT environments, reduce vendor sprawl, and streamline management. As zero-trust principles gain traction, integrated identity verification and access control within SASE frameworks help limit unauthorized movement and reduce credential-based risks.
The security delivered as a service accounted for 52% share in 2025 and is forecast to reach USD 10.4 billion by 2035. Enterprises are increasingly relying on cloud-native security services to replace traditional models, improving protection while supporting hybrid and cloud-first operations. Advanced analytics and automation embedded within these services enhance threat detection and response efficiency.
The large enterprises represented held 72% share in 2025 and is projected to generate USD 18.3 billion by 2035. These organizations adopt SASE to address complex global operations, strict security requirements, and long deployment cycles that often extend beyond two years. High availability, scalability, customizable policies, and strong service guarantees remain key adoption drivers.
United States Secure Access Service Edge Market reached USD 753.4 million in 2025. U.S.-based organizations are rapidly modernizing security frameworks to support remote work, cloud expansion, and rising cyber risks, while aligning with national zero-trust initiatives. Demand continues to rise for cloud-native platforms that improve performance, scalability, and user experience for distributed teams.
Leading companies operating in the Global Secure Access Service Edge Market include Cisco, Zscaler, Fortinet, Palo Alto Networks, Akamai, Broadcom, Netskope, Cloudflare, and Forcepoint. Companies in the Global Secure Access Service Edge Market strengthen their market position by expanding cloud-native portfolios and emphasizing integrated security and networking capabilities. Providers focus on platform consolidation to reduce complexity for enterprise customers while improving visibility and control. Continuous investment in automation, analytics, and intelligent threat mitigation enhances operational efficiency and security outcomes. Strategic partnerships and ecosystem development enable broader service integration and faster deployment. Vendors also prioritize scalability, uptime assurance, and flexible pricing models to attract large enterprises and mid-sized organizations alike.
Table of Contents
Chapter 1 Methodology
- 1.1 Market scope and definition
- 1.2 Research design
- 1.2.1 Research approach
- 1.2.2 Data collection methods
- 1.3 Data mining sources
- 1.3.1 Global
- 1.3.2 Regional/Country
- 1.4 Base estimates and calculations
- 1.4.1 Base year calculation
- 1.4.2 Key trends for market estimation
- 1.5 Primary research and validation
- 1.5.1 Primary sources
- 1.6 Forecast
- 1.7 Research assumptions and limitations
Chapter 2 Executive Summary
- 2.1 Industry 360° synopsis, 2022 - 2035
- 2.2 Key market trends
- 2.2.1 Regional
- 2.2.2 Offering
- 2.2.3 Deployment model
- 2.2.4 Organization size
- 2.2.5 End Use
- 2.3 TAM Analysis, 2026-2035
- 2.4 CXO perspectives: Strategic imperatives
- 2.4.1 Executive decision points
- 2.4.2 Critical success factors
- 2.5 Future outlook & strategic recommendations
Chapter 3 Industry Insights
- 3.1 Industry ecosystem analysis
- 3.1.1 Supplier landscape
- 3.1.2 Profit margin analysis
- 3.1.3 Cost structure
- 3.1.4 Value addition at each stage
- 3.1.5 Factor affecting the value chain
- 3.1.6 Disruptions
- 3.2 Industry impact forces
- 3.2.1.1 Growth drivers
- 3.2.1.2 Rapid cloud and SaaS adoption
- 3.2.1.3 Expansion of remote and hybrid workforces
- 3.2.1.4 Rising cybersecurity threats and attack sophistication
- 3.2.1.5 Need to reduce security complexity and vendor sprawl
- 3.2.1.6 Acceleration of zero-trust security frameworks
- 3.2.2 Industry pitfalls and challenges
- 3.2.2.1 Integration challenges with legacy infrastructure
- 3.2.2.2 Concerns over data privacy and vendor lock-in
- 3.2.3 Market opportunities
- 3.2.3.1 Expansion into SMB and mid-market segments
- 3.2.3.2 Growing demand for AI-driven threat detection
- 3.2.3.3 Increasing adoption of edge computing applications
- 3.2.3.4 Multi-cloud and hybrid-cloud modernization initiatives
- 3.3 Growth potential analysis
- 3.4 Regulatory landscape
- 3.4.1 North America
- 3.4.1.1 U.S. - California Consumer Privacy Act
- 3.4.1.2 Canada - Personal Information Protection and Electronic Documents Act
- 3.4.2 Europe
- 3.4.2.1 UK - Data Protection Act
- 3.4.2.2 Germany - Federal Data Protection Act
- 3.4.2.3 France - Digital Republic Act
- 3.4.2.4 Italy - Personal Data Protection Code
- 3.4.2.5 Spain - Organic Law on Data Protection and Digital Rights
- 3.4.3 Asia Pacific
- 3.4.3.1 China - Personal Information Protection Law
- 3.4.3.2 Japan - Act on the Protection of Personal Information
- 3.4.3.3 India - Digital Personal Data Protection Act
- 3.4.4 Latin America
- 3.4.4.1 Brazil - General Data Protection Law
- 3.4.4.2 Mexico - Federal Law on Protection of Personal Data Held by Private Parties
- 3.4.4.3 Argentina - Personal Data Protection Law
- 3.4.5 Middle East & Africa
- 3.4.5.1 UAE - Personal Data Protection Law
- 3.4.5.2 South Africa - Protection of Personal Information Act
- 3.4.5.3 Saudi Arabia - Personal Data Protection Law
- 3.4.1 North America
- 3.5 Porter's analysis
- 3.6 PESTEL analysis
- 3.7 Technology and innovation landscape
- 3.7.1 Current technological trends
- 3.7.2 Emerging technologies
- 3.8 Cost breakdown analysis
- 3.8.1 Development cost structure
- 3.8.2 R&D cost analysis
- 3.8.3 Marketing & sales costs
- 3.9 Patent analysis
- 3.10 Case study
- 3.11 Sustainability and environmental aspects
- 3.11.1 Sustainable practices
- 3.11.2 Waste reduction strategies
- 3.11.3 Energy efficiency in production
- 3.11.4 Eco-friendly Initiatives
- 3.12 Future market outlook & opportunities
Chapter 4 Competitive Landscape, 2025
- 4.1 Introduction
- 4.2 Company market share analysis
- 4.2.1 North America
- 4.2.2 Europe
- 4.2.3 Asia Pacific
- 4.2.4 LATAM
- 4.2.5 MEA
- 4.3 Competitive analysis of major market players
- 4.4 Competitive positioning matrix
- 4.5 Strategic outlook matrix
- 4.6 Key developments
- 4.6.1 Mergers & acquisitions
- 4.6.2 Partnerships & collaborations
- 4.6.3 New Product Launches
- 4.6.4 Expansion Plans and funding
Chapter 5 Market Estimates & Forecast, By Offering, 2021 - 2034 ($Bn)
- 5.1 Key trends
- 5.2 Network as a Service
- 5.3 Security as a Service
Chapter 6 Market Estimates & Forecast, By Deployment model, 2021 - 2034 ($Bn)
- 6.1 Key trends
- 6.2 Cloud
- 6.3 On-premises
Chapter 7 Market Estimates & Forecast, By Organization size, 2021 - 2034 ($Bn)
- 7.1 Key trends
- 7.2 Large Enterprises
- 7.3 SMEs
Chapter 8 Market Estimates & Forecast, By End Use, 2022-2035 (USD Mn)
- 8.1 Key trends
- 8.2 BFSI
- 8.3 IT & Telecom
- 8.4 Retail
- 8.5 Healthcare
- 8.6 Government
- 8.7 Manufacturing
- 8.8 Energy & utilities
- 8.9 Education
- 8.10 Others
Chapter 9 Market Estimates & Forecast, By Region, 2022 - 2035 (USD Mn)
- 9.1 Key trends
- 9.2 North America
- 9.2.1 US
- 9.2.2 Canada
- 9.3 Europe
- 9.3.1 Germany
- 9.3.2 UK
- 9.3.3 France
- 9.3.4 Italy
- 9.3.5 Spain
- 9.3.6 Russia
- 9.3.7 Nordics
- 9.3.8 Portugal
- 9.3.9 Croatia
- 9.3.10 Benelux
- 9.4 Asia Pacific
- 9.4.1 China
- 9.4.2 India
- 9.4.3 Japan
- 9.4.4 Australia
- 9.4.5 South Korea
- 9.4.6 Singapore
- 9.4.7 Thailand
- 9.4.8 Indonesia
- 9.4.9 Vietnam
- 9.5 Latin America
- 9.5.1 Brazil
- 9.5.2 Mexico
- 9.5.3 Argentina
- 9.5.4 Colombia
- 9.6 MEA
- 9.6.1 South Africa
- 9.6.2 Saudi Arabia
- 9.6.3 UAE
- 9.6.4 Turkey
Chapter 10 Company Profiles
- 10.1 Global Players
- 10.1.1 Cisco
- 10.1.2 Palo Alto Networks
- 10.1.3 Fortinet
- 10.1.4 Zscaler
- 10.1.5 Cloudflare
- 10.1.6 Akamai
- 10.1.7 Broadcom VMware
- 10.1.8 Juniper Networks
- 10.1.9 Aruba Networks HPE
- 10.1.10 Verizon
- 10.1.11 AT&T Cybersecurity
- 10.1.12 Check Point Software Technologies
- 10.1.13 IBM Security
- 10.1.14 McAfee Enterprise Trellix
- 10.1.15 BT Group British Telecom
- 10.2 Regional Players
- 10.2.1 SonicWall
- 10.2.2 Forcepoint
- 10.2.3 Barracuda Networks
- 10.2.4 WatchGuard Technologies
- 10.2.5 Sophos
- 10.2.6 Sangfor Technologies
- 10.2.7 Cyberoam
- 10.2.8 SecPod
- 10.2.9 T-Systems
- 10.3 Emerging / Disruptor Players
- 10.3.1 Netskope
- 10.3.2 Cato Networks
- 10.3.3 Versa Networks
- 10.3.4 Aryaka
- 10.3.5 Perimeter 81
- 10.3.6 Tailscale
- 10.3.7 Axis Security




