PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1850046

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1850046
Cybersecurity For Cars - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030)
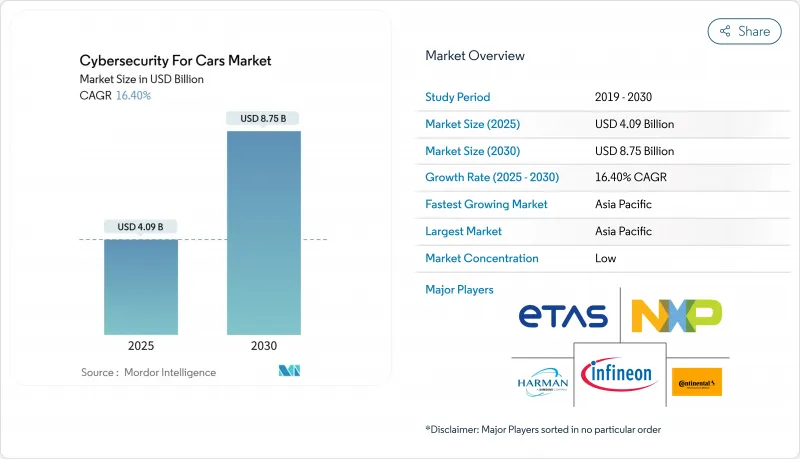
The Cybersecurity For Cars Market size is estimated at USD 4.09 billion in 2025, and is expected to reach USD 8.75 billion by 2030, at a CAGR of 16.40% during the forecast period (2025-2030).
Rapid vehicle digitalization, growing regulatory scrutiny, and wider 5G/V2X roll-outs are reshaping competitive strategies and opening new service-led revenue pools. Manufacturers race to certify Cybersecurity Management Systems before UNECE R155/R156 audits, while cloud-native security platforms gain traction as software-defined vehicles demand continuous protection. Simultaneously, electric-vehicle adoption, bidirectional charging, and sensor-rich ADAS features multiply the attack surface, attracting specialized solution vendors that promise real-time threat intelligence and automated response. OEMs also eye monetization of over-the-air security updates and usage-based insurance programs that reward certified cyber-hardening, partially offsetting high integration costs.
Global Cybersecurity For Cars Market Trends and Insights
Regulatory mandates drive fundamental change
Global homologation now hinges on demonstrating end-to-end security. UNECE R155 alone creates a USD 2.1 billion compliance opportunity by 2030 as OEMs must track 69 attack vectors and prove continuous monitoring throughout vehicle lifecycles. ISO/SAE 21434 hardcodes cybersecurity engineering into concept and decommission phases, prompting carmakers to expand specialist teams. Similar rules emerge in Japan and the United States, eliminating first-mover disadvantages and standardizing baselines worldwide.
Connected-vehicle fleet expansion multiplies attack surfaces
Modern cars host up to 150 ECUs and 100 million lines of code-volumes that could triple by 2030, stressing legacy defenses. Backend servers already account for 43% of incidents, and 95% of attacks originate remotely. 5G-based V2X exchanges add high-bandwidth vectors exposing telematics gateways, while ransomware targeting dealership IT highlights supply-chain vulnerabilities beyond the vehicle perimeter.
Legacy architecture integration costs constrain adoption
Retrofitting 150-plus ECUs in legacy platforms can add 15-20% to vehicle development budgets. Continental's 2022 breach illustrated supplier-network exposure and forced expensive architecture reviews. Such financial drag delays roll-outs among volume brands, even as compliance deadlines loom.
Other drivers and restraints analyzed in the detailed report include:
- ADAS proliferation elevates safety-critical risks
- Vehicle-to-Grid integration creates bidirectional pathways
- Automotive cybersecurity talent shortage limits execution
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Software-based platforms held 41.2% of 2024 revenue, underscoring their centrality in a software-defined vehicle era where embedded firewalls, secure firmware, and runtime intrusion detection converge. Consulting-led offerings, however, are on a 19.8% CAGR ascent as OEMs outsource gap analyses, threat modeling, and audit preparation to specialist advisors. The cybersecurity for cars market increasingly rewards vendors capable of bundling continuous monitoring with UNECE R155 documentation support, a capability visible in HARMAN's end-to-end WP.29 packages.
Professional services also orchestrate multi-vendor integration when hardware security modules, PKI suites, and cloud SOC platforms must interoperate inside tight development timelines. Such cross-domain coordination positions service providers as primary gatekeepers of compliance roadmaps, shifting revenue toward recurring assessment and managed-detection contracts. Consequently, the cybersecurity for cars market is witnessing alliances where software licensors embed service retainer clauses to secure lifetime margins.
Endpoint controls retained a 30.1% share in 2024 because cryptographic keys, secure boot, and ECU-level firewalls remain foundational. Yet cloud defenses are racing ahead at 21.3% CAGR as automakers shift data lakes, OTA orchestration, and fleet analytics off-board. The cybersecurity for cars market size for cloud protection is swelling each quarter, buoyed by collaborations such as Upstream's tie-up with Google Cloud. Incident lessons from the 2024 Volkswagen data breach showed that insufficient encryption of telemetry can cascade into reputational damage.
Network-layer segmentation and TLS v1.3 upgrades ride parallel with cloud growth, while application-centric hardening becomes imperative as vehicles download microservices weekly. Wireless security remains the final mile, guarding 5G links that now underpin platooning and V2I signalling. As virtual ECUs offload tasks to the edge, hybrid architectures combining in-vehicle enforcement with remote AI-assisted analytics form the emerging blueprint across the cybersecurity for cars market.
Cybersecurity for Cars Market is Segmented by Solution Type (Software-Based, Hardware-Based, and More), Security Type (Network Security, Application Security, and More), Vehicle Type (Passenger Cars, Light Commercial Vehicles, and More), Application (Infotainment, Telematics and Connectivity, and More), Form Type (In-Vehicle and External Cloud Services), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
Asia-Pacific commanded 35.6% revenue in 2024 and is projected to grow at 20.2% CAGR, making it the fastest-advancing geography within the cybersecurity for cars market. China's scaling of connected-EV production fuels large-scale procurement of V2G-ready PKI and ECU hardening suites, while Japan's early alignment with UNECE rules accelerates supplier certification programs. South Korea's 5G highways amplify demand for real-time over-the-air patching technologies, and India's emergent export ambitions trigger investments in ISO 21434 compliance tooling. Collectively, these dynamics push regional vendors to deliver low-latency cloud SOC services hosted within data-residency-compliant zones.
North America represents a mature yet evolving arena where premium vehicle trims and robust insurance ecosystems encourage cybersecurity monetization. The United States Connected Vehicles Rule, effective March 2025, forces OEMs to audit supply chains for sanctioned components, redirecting procurement toward domestic chipsets and security modules. Canada's tier-one suppliers leverage proximity and regulatory alignment to integrate secure Ethernet backbones, while Mexico's assembly plants adopt managed-security services to counter rising ransomware aimed at just-in-time logistics.
Europe remains a regulatory trendsetter and R&D hub. Germany hosts flagship suppliers such as Bosch ETAS and Continental, although the latter's prior breach highlighted vulnerabilities in centralized architecture. France and the United Kingdom channel public grants into quantum-safe automotive cryptography, while the ENX VCS audit framework overlays ISO 21434 to standardize supplier assessments. Eastern European engineering hubs contribute competitive talent, though war-related cyber sanctions reshape sourcing strategies.
- Continental AG
- Harman International (Samsung)
- Bosch ETAS GmbH
- Infineon Technologies AG
- NXP Semiconductors NV
- Cisco Systems Inc.
- DENSO Corporation
- Visteon Corporation
- Delphi Technologies plc
- Honeywell International Inc.
- Argus Cyber Security Ltd.
- Karamba Security Ltd.
- Arilou Technologies Ltd.
- Escrypt GmbH
- Secunet Security Networks AG
- Upstream Security Ltd.
- VicOne Inc. (Trend Micro)
- GuardKnox Cyber-Technologies Ltd.
- BlackBerry QNX
- SafeRide Technologies Ltd.
- Cybellum Technologies Ltd.
- Trillium Secure Inc.
- Vector Informatik GmbH
- Comsec Automotive Ltd.
- GuardSquare NV
- AutoCrypt Co. Ltd.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Regulatory mandates (UNECE R155/R156, ISO 21434) compliance wave
- 4.2.2 Rapid growth in connected-vehicle fleet and 5G/V2X roll-outs
- 4.2.3 ADAS/autonomous feature proliferation elevating cyber-risk
- 4.2.4 Vehicle-to-Grid (V2G) bidirectional charging introduces new attack surface
- 4.2.5 Usage-based-insurance discounts tied to certified cyber-hardening
- 4.2.6 OEM monetisation of OTA security updates in software-defined cars
- 4.3 Market Restraints
- 4.3.1 High integration cost and legacy E/E architectures
- 4.3.2 Fragmented standards and certification overload
- 4.3.3 Acute shortage of automotive-grade cyber-talent
- 4.3.4 Post-warranty liability concerns for long-life vehicles
- 4.4 Industry Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Industry Attractiveness - Porter's Five Forces Analysis
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Impact of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUES)
- 5.1 By Solution Type
- 5.1.1 Software-Based
- 5.1.2 Hardware-Based
- 5.1.3 Professional Services
- 5.1.4 Integration
- 5.1.5 Other Solutions
- 5.2 By Security Type
- 5.2.1 Network Security
- 5.2.2 Application Security
- 5.2.3 Cloud Security
- 5.2.4 Endpoint Security
- 5.2.5 Wireless Security
- 5.3 By Vehicle Type
- 5.3.1 Passenger Cars
- 5.3.2 Light Commercial Vehicles
- 5.3.3 Heavy Commercial Vehicles
- 5.3.4 Electric Vehicles (BEV/HEV/PHEV)
- 5.4 By Application
- 5.4.1 Infotainment
- 5.4.2 Telematics and Connectivity
- 5.4.3 Powertrain/Propulsion Control
- 5.4.4 ADAS and Safety
- 5.4.5 Charging Infrastructure and V2G
- 5.5 By Form Type
- 5.5.1 In-Vehicle (Embedded)
- 5.5.2 External Cloud Services
- 5.6 By Geography
- 5.6.1 North America
- 5.6.1.1 United States
- 5.6.1.2 Canada
- 5.6.1.3 Mexico
- 5.6.2 South America
- 5.6.2.1 Brazil
- 5.6.2.2 Argentina
- 5.6.2.3 Chile
- 5.6.2.4 Rest of South America
- 5.6.3 Europe
- 5.6.3.1 Germany
- 5.6.3.2 United Kingdom
- 5.6.3.3 France
- 5.6.3.4 Italy
- 5.6.3.5 Spain
- 5.6.3.6 Russia
- 5.6.3.7 Rest of Europe
- 5.6.4 Asia-Pacific
- 5.6.4.1 China
- 5.6.4.2 India
- 5.6.4.3 Japan
- 5.6.4.4 South Korea
- 5.6.4.5 Malaysia
- 5.6.4.6 Singapore
- 5.6.4.7 Australia
- 5.6.4.8 Rest of Asia-Pacific
- 5.6.5 Middle East and Africa
- 5.6.5.1 Middle East
- 5.6.5.1.1 United Arab Emirates
- 5.6.5.1.2 Saudi Arabia
- 5.6.5.1.3 Turkey
- 5.6.5.1.4 Rest of Middle East
- 5.6.5.2 Africa
- 5.6.5.2.1 South Africa
- 5.6.5.2.2 Nigeria
- 5.6.5.2.3 Rest of Africa
- 5.6.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Continental AG
- 6.4.2 Harman International (Samsung)
- 6.4.3 Bosch ETAS GmbH
- 6.4.4 Infineon Technologies AG
- 6.4.5 NXP Semiconductors NV
- 6.4.6 Cisco Systems Inc.
- 6.4.7 DENSO Corporation
- 6.4.8 Visteon Corporation
- 6.4.9 Delphi Technologies plc
- 6.4.10 Honeywell International Inc.
- 6.4.11 Argus Cyber Security Ltd.
- 6.4.12 Karamba Security Ltd.
- 6.4.13 Arilou Technologies Ltd.
- 6.4.14 Escrypt GmbH
- 6.4.15 Secunet Security Networks AG
- 6.4.16 Upstream Security Ltd.
- 6.4.17 VicOne Inc. (Trend Micro)
- 6.4.18 GuardKnox Cyber-Technologies Ltd.
- 6.4.19 BlackBerry QNX
- 6.4.20 SafeRide Technologies Ltd.
- 6.4.21 Cybellum Technologies Ltd.
- 6.4.22 Trillium Secure Inc.
- 6.4.23 Vector Informatik GmbH
- 6.4.24 Comsec Automotive Ltd.
- 6.4.25 GuardSquare NV
- 6.4.26 AutoCrypt Co. Ltd.
7 MARKET OPPORTUNITIES AND FUTURE TRENDS
- 7.1 White-Space and Unmet-Need Assessment




