PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1850212

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1850212
Cloud Encryption - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030)
The cloud encryption market stands at USD 4.90 billion in 2025 and is on course to reach USD 14.59 billion by 2030, expanding at a 24.38% CAGR.
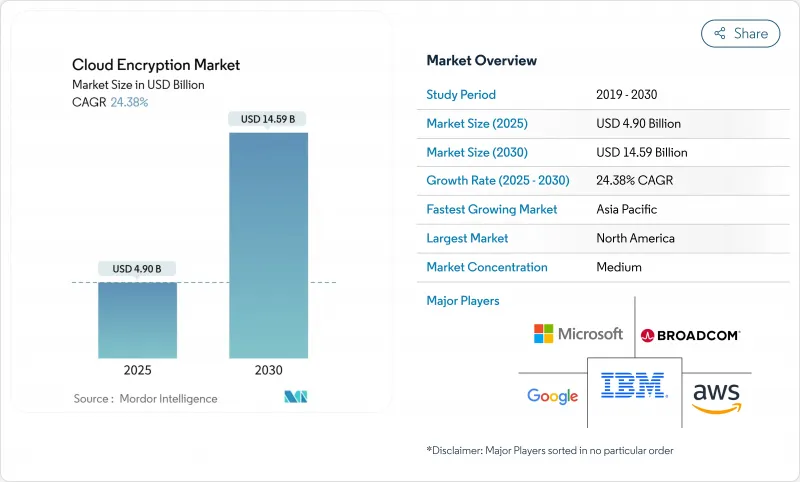
Accelerated uptake of multi-cloud strategies, rapid digital transformation among small and mid-sized enterprises, and intensifying regulatory oversight are the strongest growth catalysts. Software-defined encryption remains the architectural cornerstone, yet demand for managed services is rising quickly as organizations grapple with quantum-safe deployment, confidential-computing integrations, and multi-cloud key orchestration. Regional dynamics are equally pronounced: North America keeps the largest revenue lead, while Asia-Pacific records the fastest expansion on the back of SME cloud migrations and evolving data-sovereignty regimes. Competitive positioning hinges on end-to-end key control, post-quantum readiness, and seamless policy enforcement across heterogeneous infrastructure.
Global Cloud Encryption Market Trends and Insights
Explosion of Multi-Cloud and Edge Workloads
Enterprises now spread applications across several public clouds and edge nodes, with 86% pursuing multi-cloud strategies in 2025. Dispersed workloads shatter the traditional perimeter, forcing teams to enforce uniform encryption policies across dissimilar control planes. Edge-first architectures intensify complexity because encryption must execute with minimal latency at the data-creation point. Deep observability and AI-driven anomaly detection are therefore being embedded into encryption workflows to sustain visibility across clouds while shielding sensitive workloads from lateral movement.
Tightening Global Data-Sovereignty Laws
Regulations such as GDPR, China's PIPL, and Brazil's LGPD stipulate that data remain subject to local jurisdiction, compelling multinational firms to rethink cloud placement and key custody. Centralized key management coupled with location-aware encryption has become an indispensable compliance tool, especially where Digital Operational Resilience Act (DORA) requirements mandate demonstrable control over encryption keys held in third-party clouds. Organizations increasingly weigh repatriating high-risk workloads to sovereign facilities while maintaining selective public-cloud utilization for scalability.
High Performance Overhead in Low-Latency Apps
Real-time trading, industrial control, and immersive media demand millisecond responsiveness; yet encrypt-decrypt cycles add compute drag and jitter. Hardware offload cards and streamlined ciphers are easing the burden, but many enterprises still selectively bypass encryption in latency hotspots, exposing isolated data flows to risk. Until next-generation accelerators become ubiquitous, the tension between throughput and confidentiality will persist.
Other drivers and restraints analyzed in the detailed report include:
- SaaS Proliferation Across Regulated Verticals
- Quantum-Safe Encryption Urgency
- Key Escrow and Lifecycle Complexity
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Software controlled 64% of 2024 revenue, underscoring its foundational role in deploying at-rest and in-transit ciphers across storage, VM, and container layers. Mature toolsets bundle granular policy engines, role-based access, and AES-256 support, enabling consistent enforcement throughout DevSecOps pipelines. Vendors continuously update libraries to accommodate emerging algorithms and to embed hardware offload for performance-sensitive paths.
Services expand at a 29.10% CAGR as organizations confront cloud-native sprawl. Third-party experts design, run, and audit encryption estates spanning confidential-compute clusters, hybrid gateways, and post-quantum testbeds. Engagement scope often covers crypto-agility road mapping and zero-trust alignment, filling workforce gaps and accelerating compliance certification.
Infrastructure-layer encryption underpins every higher-order service, and IaaS retained 46% share in 2024. Customers depend on provider-supplied boot-volume ciphers, block-storage key services, and encrypted object stores to secure core compute and network constructs. Integration with organization-owned hardware security modules lets regulated workloads satisfy stringent audit demands.
SaaS encryption outpaces at 31.50% CAGR as application portfolios migrate to cloud subscription models. Each workload-customer relationship management, electronic health records, or treasury management-requires seamless data protection without altering user workflows. Providers embedding field-level encryption, bring-your-own-key frameworks, and strong certificate pinning win new customers in finance and healthcare.
The Cloud Encryption Market Report Segments the Industry Into by Component (Software, and Services), Service Model (Infrastructure-As-A-Service (IaaS), Platform-As-A-Service (PaaS), and Software-As-A-Service (SaaS)), Cloud Type (Public Cloud, Private Cloud, and Hybrid Cloud), End-User Industry (BFSI, Government and Public, and More), Enterprise Size (Large Enterprises, and Small and Medium Enterprises), and Geography.
Geography Analysis
North America held 34% of the cloud encryption market in 2024, propelled by early cloud adoption, strict sectoral mandates, and hyperscaler innovation. Financial institutions, healthcare providers, and federal agencies advance zero-trust blueprints that place encryption at every trust boundary. Collaboration between large cloud providers and NIST on post-quantum cryptography accelerates standards convergence, further entrenching the region's leadership.
Asia-Pacific delivers the fastest trajectory at 24% CAGR. SMEs constitute over 97% of businesses and are embracing cloud platforms for operational agility. National data-residency laws in China, India, and Indonesia drive demand for sovereign-ready key-management deployments. Hyperscalers respond with region-specific availability zones and partner-run key vaults, enabling customers to comply without sacrificing scalability.
Europe shoulders stringent compliance impetus under GDPR and forthcoming Digital Operational Resilience Act rules. Organizations emphasize sovereign key ownership and selective workload placement inside EU-based data centers. Sovereign cloud initiatives with in-region hardware security modules gain traction, allowing enterprises to meet legal demands while leveraging elastic compute economics.
- Amazon Web Services (AWS)
- Microsoft Corporation (Azure)
- Google LLC
- IBM Corporation
- Broadcom Inc. (Symantec)
- Trend Micro Inc.
- Cisco Systems Inc.
- Dell Technologies Inc.
- Sophos Group plc
- Hewlett Packard Enterprise
- McAfee / Skyhigh Security
- Thales Group (CipherTrust)
- Check Point Software Technologies
- Fortinet Inc.
- Oracle Corporation
- Alibaba Cloud
- Zscaler Inc.
- Protegrity
- Parablu
- Lookout Inc. (incl. CipherCloud)
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Explosion of multi-cloud and edge workloads
- 4.2.2 Tightening global data-sovereignty laws
- 4.2.3 SaaS proliferation across regulated verticals
- 4.2.4 Quantum-safe encryption urgency
- 4.2.5 Confidential-computing integrations
- 4.2.6 Gen-AI assisted key-management automation
- 4.3 Market Restraints
- 4.3.1 High performance overhead in low-latency apps
- 4.3.2 Key escrow and lifecycle complexity
- 4.3.3 Fragmented cloud-native security standards
- 4.3.4 Geo-sovereignty barriers to key export
- 4.4 Evaluation of Critical Regulatory Framework
- 4.5 Technological Outlook
- 4.6 Porter's Five Forces
- 4.6.1 Bargaining Power of Suppliers
- 4.6.2 Bargaining Power of Buyers
- 4.6.3 Threat of New Entrants
- 4.6.4 Threat of Substitutes
- 4.6.5 Competitive Rivalry
- 4.7 Impact Assessment of Key Stakeholders
- 4.8 Key Use Cases and Case Studies
- 4.9 Impact on Macroeconomic Factors of the Market
5 MARKET SIZE AND GROWTH FORECAST (VALUE)
- 5.1 By Component
- 5.1.1 Software
- 5.1.2 Services
- 5.2 By Service Model
- 5.2.1 Infrastructure-as-a-Service (IaaS)
- 5.2.2 Platform-as-a-Service (PaaS)
- 5.2.3 Software-as-a-Service (SaaS)
- 5.3 By Cloud Type
- 5.3.1 Public Cloud
- 5.3.2 Private Cloud
- 5.3.3 Hybrid Cloud
- 5.4 By End-User Industry
- 5.4.1 BFSI
- 5.4.2 Government and Public Sector
- 5.4.3 Retail and eCommerce
- 5.4.4 Healthcare and Life Sciences
- 5.4.5 Energy and Utilities
- 5.4.6 IT and Telecommunications
- 5.4.7 Others (Media, Education)
- 5.5 By Enterprise Size
- 5.5.1 Large Enterprises
- 5.5.2 Small and Medium Enterprises
- 5.6 By Geography
- 5.6.1 North America
- 5.6.1.1 United States
- 5.6.1.2 Canada
- 5.6.1.3 Mexico
- 5.6.2 South America
- 5.6.2.1 Brazil
- 5.6.2.2 Argentina
- 5.6.2.3 Rest of South America
- 5.6.3 Europe
- 5.6.3.1 United Kingdom
- 5.6.3.2 Germany
- 5.6.3.3 France
- 5.6.3.4 Italy
- 5.6.3.5 Spain
- 5.6.3.6 Nordics
- 5.6.3.7 Rest of Europe
- 5.6.4 Asia-Pacific
- 5.6.4.1 China
- 5.6.4.2 India
- 5.6.4.3 Japan
- 5.6.4.4 South Korea
- 5.6.4.5 ASEAN
- 5.6.4.6 Australia
- 5.6.4.7 New Zealand
- 5.6.4.8 Rest of Asia-Pacific
- 5.6.5 Middle East and Africa
- 5.6.5.1 Middle East
- 5.6.5.1.1 Saudi Arabia
- 5.6.5.1.2 United Arab Emirates
- 5.6.5.1.3 Turkey
- 5.6.5.1.4 Rest of Middle East
- 5.6.5.2 Africa
- 5.6.5.2.1 South Africa
- 5.6.5.2.2 Egypt
- 5.6.5.2.3 Nigeria
- 5.6.5.2.4 Rest of Africa
- 5.6.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Amazon Web Services (AWS)
- 6.4.2 Microsoft Corporation (Azure)
- 6.4.3 Google LLC
- 6.4.4 IBM Corporation
- 6.4.5 Broadcom Inc. (Symantec)
- 6.4.6 Trend Micro Inc.
- 6.4.7 Cisco Systems Inc.
- 6.4.8 Dell Technologies Inc.
- 6.4.9 Sophos Group plc
- 6.4.10 Hewlett Packard Enterprise
- 6.4.11 McAfee / Skyhigh Security
- 6.4.12 Thales Group (CipherTrust)
- 6.4.13 Check Point Software Technologies
- 6.4.14 Fortinet Inc.
- 6.4.15 Oracle Corporation
- 6.4.16 Alibaba Cloud
- 6.4.17 Zscaler Inc.
- 6.4.18 Protegrity
- 6.4.19 Parablu
- 6.4.20 Lookout Inc. (incl. CipherCloud)
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-need Assessment




