PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1851660

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1851660
File Integrity Monitoring - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030)
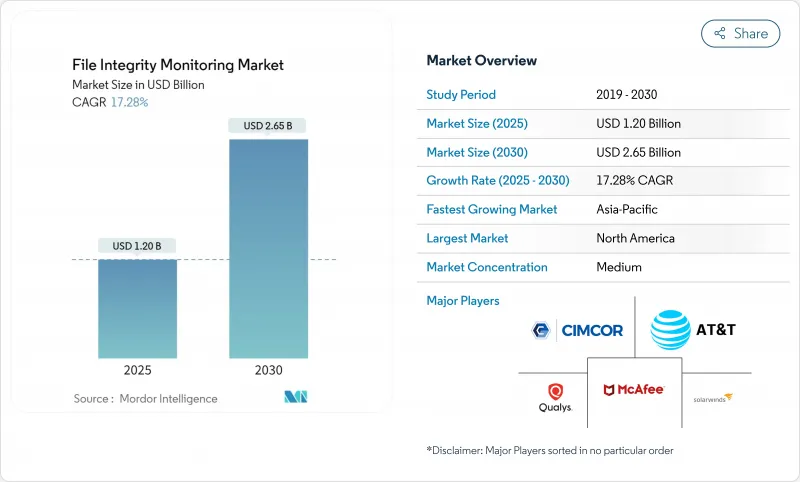
The file integrity monitoring market stands at USD 1.20 billion in 2025 and is forecast to reach USD 2.65 billion by 2030, registering a robust 17.28% CAGR.
Momentum stems from tighter global cybersecurity regulations, rapid cloud workload expansion and the convergence of AI-driven security analytics that reduce alert fatigue. Enterprises are prioritizing real-time change detection because perimeter-centric controls no longer suffice against lateral attacks and ransomware. Demand also benefits from a global pivot toward zero-trust frameworks that regard file integrity monitoring as foundational for least-privilege enforcement. Across industries, rising cyber-insurance prerequisites and board-level scrutiny of operational resilience further propel the adoption of modern, cloud-native monitoring platforms.
Global File Integrity Monitoring Market Trends and Insights
Regulatory Compliance Mandates
Financial institutions face the May 2025 New York DFS Part 500 amendment that requires privileged-access oversight and multi-factor authentication, making file integrity systems critical for audit-trail evidence. The Federal Energy Regulatory Commission approved NERC CIP-015-1, extending internal monitoring to operational technology in bulk electric systems. Updated HIPAA rules add encryption and multi-factor authentication for electronic protected health information, strengthening demand for integrity monitoring in healthcare.SEC incident-disclosure rules compel listed companies to report material cyber events within four business days, driving real-time change detection requirements. Payment firms must also satisfy PCI DSS 4.0 logging and monitoring criteria by March 2025, positioning file integrity controls as core infrastructure.
Rising Data-Breach Volume and Sophistication
Average global breach costs climbed to USD 4.88 million in 2024 and are set to hit USD 5.00 million in 2025, with healthcare incidents peaking at USD 9.77 million. Credential abuse remains the dominant attack vector, often obscured in public disclosures, underscoring the value of granular file-level monitoring. Retail and hospitality operators report 39% of incidents emanating from third-party vendors, and 82% link to human error, raising urgency for supply-chain visibility. Enterprises implementing AI and automation within security operations saved USD 2.22 million per breach on average, validating investment in machine-learning-driven FIM that filters noise and accelerates response.
High Implementation and Maintenance Costs
SMEs in emerging markets often allocate under USD 500,000 a year to security, making enterprise-grade FIM difficult to justify despite rising threats. Parallel operation of legacy and modern systems during migrations doubles expenses, while skill shortages hamper efficient deployment. European firms devote 9% of IT budgets to security, yet 89% say they need more staff to meet NIS 2 mandates, highlighting cost-driven adoption barriers.
Other drivers and restraints analyzed in the detailed report include:
- Cloud Workload Expansion Needs Cloud-Native FIM
- AI-Driven Noise-Reduction Boosting ROI
- Container and Micro-Services Blind-Spots
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Large enterprises generated over three-quarters of 2024 revenue, underlining how regulatory scrutiny and complex hybrid environments drive sizeable deployments. These organizations run distributed data centers and multicloud estates that require continuous change detection across thousands of endpoints. Financial muscle also allows investment in AI-powered analytics that shrink false-positive rates and accelerate response. Meanwhile, SMEs post the fastest 17.40% CAGR, powered by subscription-based platforms that compress onboarding time and outsource upkeep. Government grants in Asia Pacific lower the initial outlay, while cyber-insurance carriers increasingly stipulate file integrity controls for policy issuance.
The SME opportunity is being unlocked by wizard-driven setup interfaces, managed services and usage-based pricing that sidestep heavy capital expense. Yet budget and talent gaps persist; many small firms still operate without dedicated security staff and therefore rely on provider expertise for tuning and incident handling. Vendors respond with curated rule sets, automated baselining and AI-guided investigation workflows that compress skill requirements while maintaining audit-ready evidence.
Cloud offerings held 69.20% revenue in 2024 and lead growth at an 18.90% CAGR, reflecting the broader enterprise refactoring toward SaaS and infrastructure-as-code. Modern platforms deliver elastic scale and API integration, letting security teams inherit native telemetry from hyperscale providers and layer integrity assessments without agent sprawl. Unified dashboards simplify compliance mapping across PCI, GDPR and HIPAA frameworks.
On-premises tools remain relevant for highly regulated institutions that must maintain data sovereignty or segmented networks. Hybrid deployments bridge those demands by feeding on-premises logs into cloud-hosted analytics engines. As an illustration, OkCupid's migration to AWS leveraged Terraform to spin up a cloud-native FIM pipeline with minimal custom code and lower total cost than commercial alternatives. The convergence of cloud security posture management with file integrity functionality is blurring product boundaries and further accelerating migration to SaaS.
File Integrity Monitoring Market is Segmented by Organization Size (Small and Medium Enterprises, Large Enterprises), Deployment Type (On-Premise, Cloud), Installation Mode (Agent-Based, Agentless/Cloud Native), End-User Industry (Retail, BFSI, Hospitality, Healthcare, Government, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America generated 28.9% of 2024 revenue on the back of mature cyber regulations and heavy security spending by Fortune 1000 enterprises. The United States channels more than 40% of global cybersecurity budgets, and financial institutions carve out double-digit IT allocations for protection, ensuring continued leadership. Canada promotes harmonized breach-notification requirements, and Mexico's fintech law raises baseline security obligations, reinforcing regional demand.
Asia Pacific is the fastest-growing territory at 17.2% CAGR as governments digitize services and invest in sovereign cloud. Japan's first cybersecurity-focused investment fund and partnerships such as S&J with Cyleague HD expand managed detection capacity, highlighting a sophisticated buyer market. China's data-localization norms spur domestic vendors to build compliance-ready FIM for critical industries. ASEAN's finance hubs, led by Singapore, adopt advanced monitoring to support digital banking growth.
- McAfee
- Cimcor
- Qualys
- ATandT
- SolarWinds
- LogRhythm
- New Net Technologies
- Trend Micro
- Trustwave
- Ionx Solutions
- Splunk
- Software Diversified Services
- IBM
- Securonix
- Bitdefender
- Tripwire
- Rapid7
- Wazuh
- ManageEngine (Zoho)
- Tanium
- Netwrix
- Cisco Systems
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Regulatory compliance mandates
- 4.2.2 Rising data-breach volume and sophistication
- 4.2.3 Cloud workload expansion needs cloud-native FIM
- 4.2.4 SME adoption of affordable SaaS FIM
- 4.2.5 DevSecOps pipeline integration for code integrity
- 4.2.6 AI-driven noise-reduction boosting ROI
- 4.3 Market Restraints
- 4.3.1 High implementation and maintenance costs
- 4.3.2 Operational alert fatigue and skill shortage
- 4.3.3 Container and micro-services blind-spots
- 4.3.4 Shift to immutable infrastructure lowering need for file-level monitoring
- 4.4 Supply-Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Bargaining Power of Suppliers
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Assesment of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Organization Size
- 5.1.1 Small and Medium Enterprises
- 5.1.2 Large Enterprises
- 5.2 By Deployment Type
- 5.2.1 On-Premise
- 5.2.2 Cloud
- 5.3 By Installation Mode
- 5.3.1 Agent-Based
- 5.3.2 Agentless / Cloud Native
- 5.4 By End-user Industry
- 5.4.1 Retail
- 5.4.2 BFSI
- 5.4.3 Hospitality
- 5.4.4 Healthcare
- 5.4.5 Government
- 5.4.6 Entertainment and Media
- 5.4.7 Other Industries
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 South America
- 5.5.2.1 Brazil
- 5.5.2.2 Argentina
- 5.5.2.3 Rest of South America
- 5.5.3 Europe
- 5.5.3.1 Germany
- 5.5.3.2 United Kingdom
- 5.5.3.3 France
- 5.5.3.4 Netherlands
- 5.5.3.5 Rest of Europe
- 5.5.4 Asia-Pacific
- 5.5.4.1 China
- 5.5.4.2 Japan
- 5.5.4.3 India
- 5.5.4.4 South Korea
- 5.5.4.5 Australia and New Zealand
- 5.5.4.6 Rest of Asia-Pacific
- 5.5.5 Middle East and Africa
- 5.5.5.1 Middle East
- 5.5.5.1.1 United Arab Emirates
- 5.5.5.1.2 Saudi Arabia
- 5.5.5.1.3 Turkey
- 5.5.5.1.4 Rest of Middle East
- 5.5.5.2 Africa
- 5.5.5.2.1 South Africa
- 5.5.5.2.2 Nigeria
- 5.5.5.2.3 Rest of Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 McAfee
- 6.4.2 Cimcor
- 6.4.3 Qualys
- 6.4.4 ATandT
- 6.4.5 SolarWinds
- 6.4.6 LogRhythm
- 6.4.7 New Net Technologies
- 6.4.8 Trend Micro
- 6.4.9 Trustwave
- 6.4.10 Ionx Solutions
- 6.4.11 Splunk
- 6.4.12 Software Diversified Services
- 6.4.13 IBM
- 6.4.14 Securonix
- 6.4.15 Bitdefender
- 6.4.16 Tripwire
- 6.4.17 Rapid7
- 6.4.18 Wazuh
- 6.4.19 ManageEngine (Zoho)
- 6.4.20 Tanium
- 6.4.21 Netwrix
- 6.4.22 Cisco Systems
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-need Assessment




