PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1906154

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1906154
Identity Governance And Administration - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2026 - 2031)
The identity governance and administration market size in 2026 is estimated at USD 9.59 billion, growing from 2025 value of USD 8.36 billion with 2031 projections showing USD 19.12 billion, growing at 14.82% CAGR over 2026-2031.
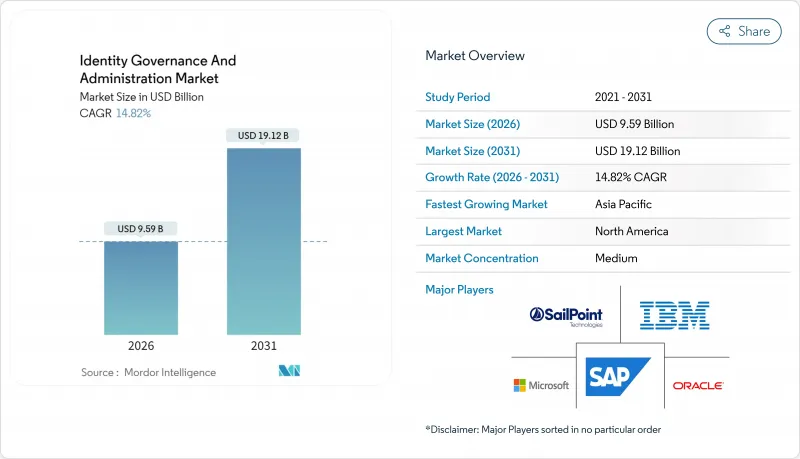
Heightened reliance on hybrid IT estates combined with an 82% surge in impersonation-led fraud is steering security spending toward identity-centric controls.Cloud delivery models now anchor most new deployments, reflecting the need for elastic scaling and quicker time-to-value. Regional spending patterns are fragmenting: North America sets the adoption pace through mature zero-trust programs, while Asia propels overall growth as local enterprises accelerate digitization and leapfrog to cloud-native tools. Services retain the largest revenue pool, mirroring the skills gap that hampers in-house roll-outs and drives demand for managed identity expertise. Meanwhile, vendors are embedding machine learning into certification workflows, automating entitlement reviews and raising detection accuracy, a shift that is rapidly altering competitive positioning and widening addressable opportunities in adjacent privileged access and non-human identity segments.
Global Identity Governance And Administration Market Trends and Insights
Rising Adoption of AI-Driven IGA for Continuous Access Certification
AI-enabled tools now inspect user and non-human entitlements in near real time, minimizing certification fatigue by spotlighting high-risk anomalies. Enterprises deploying these capabilities report sharper risk detection and administrative cost relief, a combination that scales governance to sprawling multicloud estates. Generative AI is also rewriting complex entitlement descriptions into natural language, widening participation among business managers and reducing help-desk cycles. Early roll-outs in financial services and tech verticals suggest the model is suited for globally dispersed workforces where manual reviews have become impractical. Growth momentum is therefore expected to intensify as more organizations build trust in explainable AI review engines.
Convergence of PAM & IGA Suites Among Highly-Regulated Sectors in Europe
Financial institutions and critical infrastructure operators are rationalizing tool sprawl by fusing privileged access controls with broader lifecycle governance. Unified suites reduce overlap between administrator and standard user entitlements, closing gaps that attackers target. Recent acquisitions by leading PAM providers underscore a race to integrate governance modules and to deliver compliance-ready workflows aligned with Europe's Digital Operational Resilience Act. Early adopters report fewer audit findings and faster evidence gathering, reinforcing the business case for integrated architectures across global subsidiaries.
Skill Shortage in Identity Engineering Limiting Complex Deployments
Demand for specialists versed in directory architecture, entitlement modelling, and regulatory mapping continues to outstrip supply. A majority of enterprises cite talent scarcity as the principal hurdle to large-scale implementations. The gap drives wage inflation and elongates project timelines, especially in emerging markets where cybersecurity skill pools remain shallow. Vendors are responding with prescriptive templates and managed offerings, yet many organizations still defer advanced features such as policy automation because internal expertise is absent.
Other drivers and restraints analyzed in the detailed report include:
- Zero-Trust & Passwordless Initiatives Accelerating Role Mining Tools in North America
- M&A Activity Among Telcos Driving Telco-Grade IGA Roll-Outs in APAC
- API-Sprawl Elevating Integration Cost for Brownfield IT Environments
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Services generated 56.42% of 2025 revenue in the identity governance and administration market, reflecting the consulting and integration effort needed to harmonize diverse application estates. Implementers remain indispensable for mapping entitlements across on-premises, SaaS, and operational technology layers, particularly in regulated sectors that demand audit-grade evidence. The arrival of SaaS-delivered governance platforms is shifting some expenditure toward outcome-based managed services, with providers bundling software subscriptions and day-to-day administration into fixed-fee models.
Software subscriptions are, however, outpacing services in growth terms. AI-enhanced user provisioning, continuous certification, and privileged session analytics underpin a 17.25% CAGR outlook, drawing budget from stand-alone access management tools. Vendors are weaving automation into every workflow, shrinking manual touchpoints, and opening mid-market opportunities where previous complexity deterred adoption. This dynamic positions software to capture incremental share as customers seek long-term cost efficiencies.
Cloud deployments accounted for 60.74% of the identity governance and administration market size in 2025 and are projected to register the segment's steepest 16.02% CAGR. Enterprises value rapid onboarding, elastic scaling, and instant access to feature releases. Multicloud realities now require governance that spans infrastructure-as-a-service, SaaS, and platform services, making centrally-hosted architectures the preferred option.
On-premises installations persist where data-sovereignty statutes or air-gapped environments dictate local control. Sovereign-cloud constructs are narrowing this divide by offering dedicated regional instances that satisfy residency rules without sacrificing subscription economics. Hybrid models, in which policy engines run in the cloud while sensitive identity stores remain on-site, provide transitional paths for organizations with large legacy footprints.
The Identity Governance and Administration Market Report is Segmented by Component (Solutions, Services), Deployment Mode (On Premise, Cloud), Enterprise Size (Large Enterprises, Small and Medium Enterprises), End User Vertical (Banking, Financial Services, and Insurance, IT and Telecom, Energy and Utilities, Government and Public Defense, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America generated 32.54% of 2025 revenue, underpinned by mature zero-trust initiatives and a concentration of platform vendors that continually innovate around AI-driven analytics. Sector-specific mandates in financial services and healthcare boost baseline demand, while government agencies sponsor large-scale reference deployments that de-risk adoption for private firms.
Asia-Pacific is projected to expand at a 16.75% CAGR, buoyed by aggressive digital-economy policies in China, India, and key ASEAN states. Telco consolidation, sovereign-cloud investments, and widespread mobile-first consumer services force enterprises to modernize identity controls rapidly. Domestic software suppliers leverage localisation advantages to penetrate accounts subject to national technology-development directives, amplifying competitive intensity.
Europe remains a pivotal battleground where GDPR, sectoral directives, and ESG-linked procurement rules compel organisations to adopt audit-ready governance. The Nordics push vendor assessment rigor even further, embedding ethical identity verification into sourcing checklists. Meanwhile, the Middle East prioritises residency-compliant cloud instances to harmonise expansive e-government projects with data-sovereignty imperatives. South America and Africa enter the market through banking, telecom, and public-sector pilots that demonstrate rapid ROI and spur broader adoption.
- SailPoint Technologies Holdings Inc.
- IBM Corporation
- Microsoft Corporation
- Oracle Corporation
- Broadcom Inc. (CA Technologies)
- SAP SE
- Okta Inc.
- One Identity LLC
- Saviynt Inc.
- CyberArk Software Ltd.
- Ping Identity Holding Corp.
- ForgeRock (Thales Group)
- Hitachi ID Systems
- Evidian (Atos)
- Quest Software Inc.
- Micro Focus (OpenText)
- RSA Security LLC
- Wipro Limited
- Cognizant Technology Solutions Corp.
- Omada Identity
- Zilla Security
- SecZetta
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Rising Adoption of AI-driven IGA for Continuous Access Certification
- 4.2.2 Convergence of PAM and IGA Suites Among Highly-Regulated Sectors in Europe
- 4.2.3 Zero-Trust and Passwordless Initiatives Accelerating Role Mining Tools in North America
- 4.2.4 MandA Activity Among Telcos Driving Telco-grade IGA Roll-outs in APAC
- 4.2.5 Sovereign-Cloud Mandates Fueling Domestic IGA Platforms in Middle East
- 4.2.6 ESG-Linked Vendor Assessment Requirements Pushing Audit-grade Identity Proof in Nordics
- 4.3 Market Restraints
- 4.3.1 Skill Shortage in Identity Engineering Limiting Complex Deployments
- 4.3.2 API-Sprawl Elevating Integration Cost for Brownfield IT Environments
- 4.3.3 Fragmented Data-Residency Laws Slowing Global Rollouts for Multinationals
- 4.3.4 Delayed ROI from Role-Based Access Clean-ups in Legacy ERP Estates
- 4.4 Value / Supply-Chain Analysis
- 4.5 Regulatory Outlook
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Investment Analysis
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.1.1 Access Certification and Review
- 5.1.1.2 User Provisioning / De-provisioning
- 5.1.1.3 Privileged Governance
- 5.1.1.4 Password Management
- 5.1.2 Services
- 5.1.2.1 Professional Services
- 5.1.2.2 Managed Services
- 5.1.1 Solutions
- 5.2 By Deployment Mode
- 5.2.1 On-premise
- 5.2.2 Cloud
- 5.3 By Enterprise Size
- 5.3.1 Large Enterprises
- 5.3.2 Small and Medium Enterprises
- 5.4 By End-user Vertical
- 5.4.1 Banking, Financial Services and Insurance
- 5.4.2 IT and Telecom
- 5.4.3 Healthcare and Life Sciences
- 5.4.4 Energy and Utilities
- 5.4.5 Government and Public Defense
- 5.4.6 Manufacturing
- 5.4.7 Retail and e-Commerce
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 South America
- 5.5.2.1 Brazil
- 5.5.2.2 Argentina
- 5.5.2.3 Rest of South America
- 5.5.3 Europe
- 5.5.3.1 United Kingdom
- 5.5.3.2 Germany
- 5.5.3.3 France
- 5.5.3.4 Italy
- 5.5.3.5 Nordics (Sweden, Norway, Denmark, Finland)
- 5.5.3.6 Rest of Europe
- 5.5.4 APAC
- 5.5.4.1 China
- 5.5.4.2 India
- 5.5.4.3 Japan
- 5.5.4.4 South Korea
- 5.5.4.5 ASEAN (Singapore, Indonesia, Malaysia, Thailand, Vietnam, Philippines)
- 5.5.4.6 Rest of APAC
- 5.5.5 Middle East
- 5.5.5.1 GCC (Saudi Arabia, UAE, Qatar, Oman, Kuwait, Bahrain)
- 5.5.5.2 Turkey
- 5.5.5.3 Rest of Middle East
- 5.5.6 Africa
- 5.5.6.1 South Africa
- 5.5.6.2 Nigeria
- 5.5.6.3 Rest of Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global-level Overview, Market-level Overview, Core Segments, Financials, Strategic Information, Market Rank/Share, Products and Services, Recent Developments)
- 6.4.1 SailPoint Technologies Holdings Inc.
- 6.4.2 IBM Corporation
- 6.4.3 Microsoft Corporation
- 6.4.4 Oracle Corporation
- 6.4.5 Broadcom Inc. (CA Technologies)
- 6.4.6 SAP SE
- 6.4.7 Okta Inc.
- 6.4.8 One Identity LLC
- 6.4.9 Saviynt Inc.
- 6.4.10 CyberArk Software Ltd.
- 6.4.11 Ping Identity Holding Corp.
- 6.4.12 ForgeRock (Thales Group)
- 6.4.13 Hitachi ID Systems
- 6.4.14 Evidian (Atos)
- 6.4.15 Quest Software Inc.
- 6.4.16 Micro Focus (OpenText)
- 6.4.17 RSA Security LLC
- 6.4.18 Wipro Limited
- 6.4.19 Cognizant Technology Solutions Corp.
- 6.4.20 Omada Identity
- 6.4.21 Zilla Security
- 6.4.22 SecZetta
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment




