PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1849970

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1849970
Cloud Security Software - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030)
The cloud security software market currently generates USD 50.11 billion and is projected to reach USD 95.03 billion by 2030, advancing at a 13.7% CAGR.
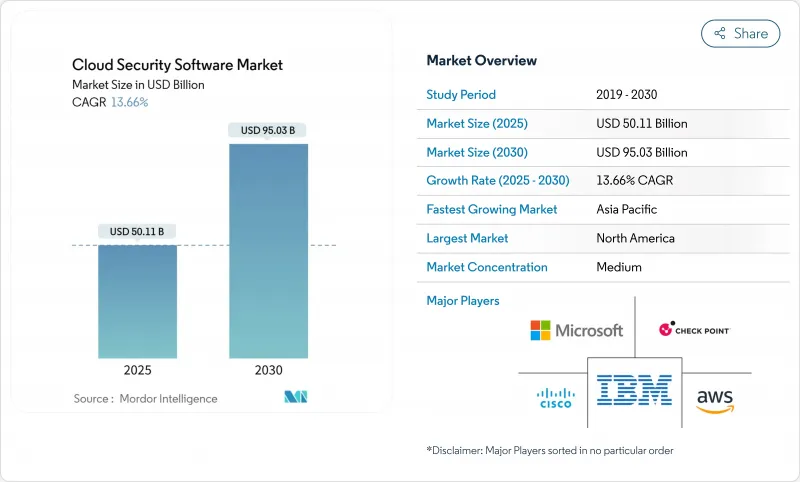
This growth trajectory confirms a robust cloud security software market size that is shaped by regulated industries racing to modernize digital infrastructure, the embrace of zero-trust frameworks, and the emergence of generative-AI-driven threats. Heightened compliance obligations, sovereign-cloud policies, and capital spending by hyperscalers have amplified demand for unified security orchestration across multi-cloud deployments. As enterprises shift critical workloads to the public cloud, they prioritize identity management, runtime protection, and automated compliance reporting to streamline risk management and sustain business velocity. Vendor competition now centers on platform consolidation and native AI capabilities that promise faster detection, lower false-positive rates, and seamless integration across diverse cloud environments.
Global Cloud Security Software Market Trends and Insights
Fast-growing Public-cloud Adoption Among Regulated Industries
Regulated enterprises are re-tooling legacy architectures as supervisory bodies update cloud guidance. The Federal Financial Institutions Examination Council now stresses real-time third-party risk monitoring, prompting banks and insurers to adopt automated controls that verify compliance evidence continuously. Healthcare providers likewise align modernization plans with security certifications that deliver competitive benefit rather than mere regulatory box-ticking. Federal Risk and Authorization Management Program reforms further legitimize cloud migrations, cascading adoption expectations across contractors and suppliers. Vendors respond with pre-packaged compliance templates that shorten onboarding times and translate policy into programmatic guardrails across multi-cloud estates.
Surge in Multi-cloud and Hybrid-cloud Complexity
Enterprises typically run workloads on 3.2 cloud providers, multiplying policy silos and integration debt. Disparate APIs and variable security models fuel demand for centralized orchestration able to normalize controls independent of underlying infrastructure. Cloud-native application protection platforms thus gain favor by detecting misconfigurations and runtime anomalies across containers and serverless functions. Organizations originally pursued multi-cloud for diversification but now rely on orchestration to maintain operational viability as cost, performance, and jurisdictional requirements diverge.
Integration Debt with Legacy Security Stacks
Security leaders grapple with duplicated tooling and inconsistent policies as cloud controls overlay on-premises investments. Parallel environments obscure attack paths and inflate operating costs, especially when organizations retrofit zero-trust models onto hub-and-spoke networks. Without unified telemetry, threat intelligence remains siloed, and remediation cycles extend, undermining return on security spend.
Other drivers and restraints analyzed in the detailed report include:
- Zero-trust Architecture Mandates
- Generative-AI-driven Threat Vectors
- Cloud-native Skills Shortage
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Cloud Identity and Access Management accounted for a 34.8% cloud security software market share in 2024, reflecting its cornerstone role in zero-trust rollouts. The segment's entrenched status underpins the broader cloud security software market as organizations prioritize least-privilege policies to mitigate lateral movement risks. Simultaneously, Cloud-Native Application Protection Platforms and Cloud Workload Protection Platforms achieve a 14.5% CAGR through 2030, mirroring the proliferation of containerized workloads that require runtime safeguards. Their ascent joins Cloud Access Security Brokers and vulnerability scanners that integrate within DevSecOps pipelines, offering continuous assessment across development and production.
Demand for unified logging drives Security Information and Event Management modernization, with platforms leveraging machine learning to parse cloud-scale telemetry and accelerate mean-time-to-detect. Vendors further experiment with quantum-resistant algorithms, as demonstrated by SEALSQ's Crystal Kyber and Crystal Dilithium showcase, signaling the long-term evolution of encryption boundaries. These innovations collectively reshape category borders, encouraging platform vendors to fold adjacent capabilities into consolidated suites for simplified procurement and operations.
Public cloud retained 65.4% share of the cloud security software market size in 2024, buoyed by hyperscaler investments that reached USD 215 billion in 2025. Amazon alone allocated more than USD 75 billion, augmenting native security services and geographic redundancy. Despite public cloud scale advantages, hybrid and multi-cloud environments post the fastest 15.2% CAGR as enterprises seek workload portability, data residency assurance, and cost optimization.
Hybrid complexity magnifies the need for policy abstraction, prompting security providers to offer central dashboards that push uniform rules across Kubernetes clusters, SaaS applications, and on-premises assets. Private cloud adoption persists among industries with sensitive intellectual property or latency-critical workloads, though many treat private environments as transitional waypoints toward broader public adoption once compliance hurdles ease.
The Cloud Security Software Market Report is Segmented by Software (Cloud IAM, CASB, CNAPP / CWPP, and More), Deployment Mode (Public Cloud, Private Cloud, and Hybrid / Multi-Cloud), Organization Size (Large Enterprises and Small and Medium Enterprises (SMEs)), End-User Industry (BFSI, IT and Telecom, Healthcare and Life-Sciences, and More), and Geography.
Geography Analysis
North America retained a 41.3% revenue share in 2024, signifying the largest regional slice of the cloud security software market. Federal Risk and Authorization Management Program modernization boosts confidence in cloud controls across civilian agencies, contractors, and heavily regulated industries. Concurrently, the U.S. Department of Justice Data Security Program introduces fresh compliance layers for telecommunications firms handling foreign data traffic, generating opportunities for automated policy-mapping tools that reconcile overlapping rule sets.
Asia-Pacific is the fastest-growing territory with a 14.7% CAGR through 2030, underpinned by sovereign-cloud directives, 5G rollout, and broad-scale digitization. Yet acute talent shortages threaten execution timelines. Japan's skills deficit underscores the training imperative, spurring partnerships between universities, cloud providers, and security vendors to expand certification access. China advances domestically sourced security stacks to meet sovereignty mandates, whereas India emphasizes low-cost, scalable solutions to service a diverse enterprise base. Australia, New Zealand, and South Korea leverage advanced network infrastructure to adopt real-time threat detection platforms that ensure low-latency protection for financial trading and smart-factory environments.
Europe navigates the delicate balance between innovation and sovereignty. General Data Protection Regulation and the evolving Network and Information Security Directive shape procurement criteria that favor providers offering data-localization options and transparent audit trails. Germany leads adoption in manufacturing, while France invests in nationally hosted cloud zones to underpin critical infrastructure projects. Post-Brexit, the United Kingdom crafts its own data security stance yet aligns closely enough to facilitate cross-border transfers. Regional harmonization efforts simplify vendor entry, although divergent national timelines for directive transposition continue to complicate uniform rollout strategies.
- Palo Alto Networks
- Cisco Systems
- Fortinet
- Zscaler
- Check Point Software
- IBM
- Broadcom (CA Technologies)
- Microsoft
- Trend Micro
- Okta
- CrowdStrike
- Rapid7
- Amazon Web Services (Security services)
- Google Cloud Security
- HPE (Aruba)
- Proofpoint
- Sophos
- Imperva
- Netskope
- Qualys
- F5 Networks
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Fast-growing public-cloud adoption among regulated industries
- 4.2.2 Surge in multi-cloud and hybrid-cloud complexity
- 4.2.3 Zero-trust architecture mandates
- 4.2.4 Generative-AI-driven threat vectors
- 4.2.5 Cyber-insurance premium incentives
- 4.2.6 Sovereign-cloud initiatives in EU and APAC
- 4.3 Market Restraints
- 4.3.1 Integration debt with legacy security stacks
- 4.3.2 Cloud-native skills shortage
- 4.3.3 Compliance conflicts across jurisdictions
- 4.3.4 Persistent shadow-IT and BYOD behaviour
- 4.4 Value Chain Analysis
- 4.5 Regulatory and Compliance Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Software
- 5.1.1 Cloud IAM
- 5.1.2 CASB
- 5.1.3 CNAPP / CWPP
- 5.1.4 Vulnerability and Risk Management
- 5.1.5 Web, Email and DNS Security
- 5.1.6 SIEM and Log Management
- 5.2 By Deployment Mode
- 5.2.1 Public Cloud
- 5.2.2 Private Cloud
- 5.2.3 Hybrid / Multi-Cloud
- 5.3 By Organization Size
- 5.3.1 Large Enterprises
- 5.3.2 Small and Medium Enterprises (SMEs)
- 5.4 By End-User Industry
- 5.4.1 BFSI
- 5.4.2 IT and Telecom
- 5.4.3 Healthcare and Life-Sciences
- 5.4.4 Retail and Consumer Goods
- 5.4.5 Manufacturing
- 5.4.6 Others
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 Europe
- 5.5.2.1 Germany
- 5.5.2.2 United Kingdom
- 5.5.2.3 France
- 5.5.2.4 Italy
- 5.5.2.5 Spain
- 5.5.2.6 Russia
- 5.5.2.7 Rest of Europe
- 5.5.3 Asia-Pacific
- 5.5.3.1 China
- 5.5.3.2 Japan
- 5.5.3.3 India
- 5.5.3.4 South Korea
- 5.5.3.5 Australia and New Zealand
- 5.5.3.6 Rest of Asia-Pacific
- 5.5.4 South America
- 5.5.4.1 Brazil
- 5.5.4.2 Argentina
- 5.5.4.3 Rest of South America
- 5.5.5 Middle East and Africa
- 5.5.5.1 Middle East
- 5.5.5.1.1 Saudi Arabia
- 5.5.5.1.2 United Arab Emirates
- 5.5.5.1.3 Turkey
- 5.5.5.1.4 Rest of Middle East
- 5.5.5.2 Africa
- 5.5.5.2.1 South Africa
- 5.5.5.2.2 Nigeria
- 5.5.5.2.3 Rest of Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Palo Alto Networks
- 6.4.2 Cisco Systems
- 6.4.3 Fortinet
- 6.4.4 Zscaler
- 6.4.5 Check Point Software
- 6.4.6 IBM
- 6.4.7 Broadcom (CA Technologies)
- 6.4.8 Microsoft
- 6.4.9 Trend Micro
- 6.4.10 Okta
- 6.4.11 CrowdStrike
- 6.4.12 Rapid7
- 6.4.13 Amazon Web Services (Security services)
- 6.4.14 Google Cloud Security
- 6.4.15 HPE (Aruba)
- 6.4.16 Proofpoint
- 6.4.17 Sophos
- 6.4.18 Imperva
- 6.4.19 Netskope
- 6.4.20 Qualys
- 6.4.21 F5 Networks
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-need Assessment




