PUBLISHER: Global Market Insights Inc. | PRODUCT CODE: 1833452

PUBLISHER: Global Market Insights Inc. | PRODUCT CODE: 1833452
Data Center Logical Security Market Opportunity, Growth Drivers, Industry Trend Analysis, and Forecast 2025 - 2034
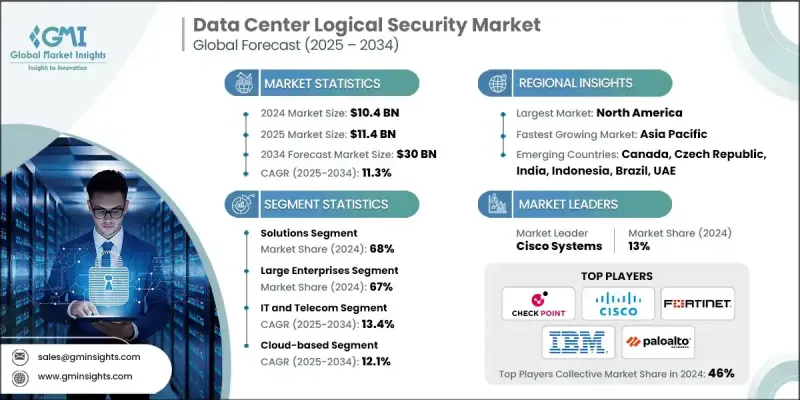
The Global Data Center Logical Security Market was valued at USD 10.4 billion in 2024 and is estimated to grow at a CAGR of 11.3% to reach USD 30 billion by 2034.
As cyber threats evolve and digital transformation accelerates, security within data centers has become a core pillar of operational trust and business continuity rather than just a perimeter-based requirement. Organizations are shifting their strategies to embrace integrated platforms that enable automated threat detection, proactive compliance, and comprehensive protection across hybrid and multi-cloud environments. The adoption of cloud-native security architectures, artificial intelligence, and zero-trust frameworks is helping businesses address stricter global data protection laws and ensure compliance. The tightening of regulatory mandates worldwide has created increased demand for encryption technologies, identity-driven security models, and micro-segmentation. This has opened up collaboration opportunities among cybersecurity providers, compliance specialists, and data center operators to create highly customized logical security frameworks tailored to sector-specific and regional requirements. Additionally, increased cloud adoption and the rise of software-defined networking (SDN) are driving the deployment of security information and event management (SIEM) and intrusion detection/prevention systems (IDS/IPS), as enterprises seek more agile, automated security solutions to stay ahead of sophisticated threats.
| Market Scope | |
|---|---|
| Start Year | 2024 |
| Forecast Year | 2025-2034 |
| Start Value | $10.4 Billion |
| Forecast Value | $30 Billion |
| CAGR | 11.3% |
The solutions segment held a 68% share in 2024 and is projected to grow at a CAGR of 10% through 2034. These solutions are increasingly integrating generative AI and machine learning technologies, shifting the security approach from reactive detection to initiative-taking remediation and autonomous threat prevention. These AI-powered systems can conduct automated threat hunting, simplifying complex cyberattack scenarios, and initiating real-time response actions with minimal human intervention. This evolution is crucial for protecting large-scale, fast-changing data center environments, closing the cybersecurity skills gap, and defending against advanced threat actors through predictive, self-healing security infrastructures.
The large enterprises segment held 67% share in 2024 and is forecasted to grow at a CAGR of 10% between 2025 and 2034. These organizations dominate due to their ability to invest in premium, integrated security platforms from leading vendors like Juniper, Trend Micro, Fortinet, and Broadcom. With vast digital footprints and complex compliance requirements, large enterprises require high-performance security solutions and centralized management systems. Their capacity to absorb implementation costs and manage sophisticated environments pushes vendors to prioritize their security demands, effectively shaping the broader market landscape.
North America Data Center Logical Security Market held 37.7% share in 2024. The widespread implementation of Zero Trust security models in the region is reshaping how data centers are secured. These models enforce strict access controls, constant monitoring, and granular security policies, significantly reducing risk. With sectors such as healthcare, insurance, and finance increasingly relying on Zero Trust, it is expected to become the foundational model for logical security across the region, as organizations face both internal vulnerabilities and external threats.
Key players shaping the Data Center Logical Security Market include Palo Alto Networks, Cisco Systems, McAfee, IBM, Fortinet, Hewlett Packard Enterprise, Check Point Software Technologies, Continental, Juniper, Trend Micro, and Broadcom. These companies are leading the charge in offering comprehensive, AI-enabled security solutions tailored for modern data center environments. To reinforce their position in the market, companies in the data center logical security industry are adopting several critical strategies. They are focusing heavily on R&D to develop AI-driven, self-healing security solutions capable of autonomous threat detection and real-time response.
Table of Contents
Chapter 1 Methodology
- 1.1 Market scope and definition
- 1.2 Research design
- 1.2.1 Research approach
- 1.2.2 Data collection methods
- 1.3 Data mining sources
- 1.3.1 Global
- 1.3.2 Regional/Country
- 1.4 Base estimates and calculations
- 1.4.1 Base year calculation
- 1.4.2 Key trends for market estimation
- 1.5 Primary research and validation
- 1.5.1 Primary sources
- 1.6 Forecast model
- 1.7 Research assumptions and limitations
Chapter 2 Executive Summary
- 2.1 Industry 360° synopsis
- 2.2 Key market trends
- 2.2.1 Regional
- 2.2.2 Solution
- 2.2.3 Organization size
- 2.2.4 End Use
- 2.2.5 Deployment
- 2.3 TAM Analysis, 2025-2034
- 2.4 CXO perspectives: strategic imperatives
- 2.4.1 Executive decision points
- 2.4.2 Critical success factors
- 2.5 Future outlook and strategic recommendations
- 2.5.1 Technology roadmap & innovation trends
- 2.5.2 Emerging use cases & applications
- 2.5.3 Next-generation data center architecture security
- 2.5.4 Artificial intelligence & machine learning integration
- 2.5.5 Autonomous security operations evolution
- 2.5.6 Post-quantum cryptography transition
Chapter 3 Industry Insights
- 3.1 Industry ecosystem analysis
- 3.1.1 Supplier landscape
- 3.1.2 Profit margin
- 3.1.3 Cost structure
- 3.1.4 Value addition at each stage
- 3.1.5 Factor affecting the value chain
- 3.1.6 Disruptions
- 3.2 Industry impact forces
- 3.2.1 Growth drivers
- 3.2.1.1 Escalating cyber threats
- 3.2.1.2 Cloud computing & hybrid environments
- 3.2.1.3 Regulatory compliance requirements
- 3.2.1.4 Zero-trust architecture adoption
- 3.2.2 Industry pitfalls and challenges
- 3.2.2.1 Integration complexity & cost
- 3.2.2.2 Cybersecurity talent shortage
- 3.2.3 Market opportunities
- 3.2.3.1 AI-driven security solutions
- 3.2.3.2 Growth in managed security services (MSS)
- 3.2.3.3 Expansion in emerging markets
- 3.2.3.4 Virtualization & edge computing security
- 3.2.1 Growth drivers
- 3.3 Growth potential analysis
- 3.4 Regulatory landscape
- 3.4.1 North America
- 3.4.2 Europe
- 3.4.3 Asia Pacific
- 3.4.4 Latin America
- 3.4.5 Middle East & Africa
- 3.5 Porter’s analysis
- 3.6 PESTEL analysis
- 3.7 Technology and innovation landscape
- 3.7.1 Current technological trends
- 3.7.1.1 Password less authentication evolution
- 3.7.1.2 Extended detection & response (XDR) evolution
- 3.7.1.3 Privacy-preserving analytics technologies
- 3.7.1.4 Container security & runtime protection
- 3.7.2 Emerging technologies
- 3.7.2.1 Decentralized identity & self-sovereign identity
- 3.7.2.2 Homomorphic encryption & confidential computing
- 3.7.2.3 Cloud security mesh architecture
- 3.7.2.4 Security service mesh implementation
- 3.7.1 Current technological trends
- 3.8 Cost breakdown analysis
- 3.9 Patent analysis
- 3.10 Use cases
- 3.10.1 Financial Services
- 3.10.2 Healthcare & Life Sciences
- 3.10.3 Government & Defense
- 3.10.4 Manufacturing & Industrial
- 3.11 Best-case scenario
- 3.12 Investment & funding trends analysis
- 3.13 Supply chain dynamics & dependencies
- 3.14 Multi-cloud security complexity analysis
- 3.15 Compliance burden assessment framework
- 3.16 Skills gap impact on security posture
- 3.17 Security debt management crisis
- 3.18 Cyber insurance impact on security investments
- 3.19 Market disruption analysis
- 3.19.1 Quantum computing impact timeline
- 3.19.2 AI-powered security revolution
- 3.19.3 Zero trust architecture mandates
- 3.19.4 Cloud-native security transformation
- 3.19.5 Privacy regulation explosion
- 3.20 Vendor selection & implementation strategy
- 3.20.1 Advanced vendor evaluation framework
- 3.20.2 Implementation best practices
- 3.20.3 Risk mitigation & management
- 3.21 Market performance & ROI analysis
- 3.21.1 Security investment ROI framework
- 3.21.2 Cost optimization strategies
- 3.21.3 Performance impact assessment
- 3.22 Sustainability and environmental aspects
- 3.22.1 Sustainable practices
- 3.22.2 Waste reduction strategies
- 3.22.3 Energy efficiency in production
- 3.22.4 Eco-friendly initiatives
- 3.22.5 Carbon footprint considerations
Chapter 4 Competitive Landscape, 2024
- 4.1 Introduction
- 4.2 Company market share analysis
- 4.2.1 North America
- 4.2.2 Europe
- 4.2.3 Asia Pacific
- 4.2.4 LATAM
- 4.2.5 MEA
- 4.3 Competitive analysis of major market players
- 4.4 Competitive positioning matrix
- 4.5 Strategic outlook matrix
- 4.6 Key developments
- 4.6.1 Mergers & acquisitions
- 4.6.2 Partnerships & collaborations
- 4.6.3 New product launches
- 4.6.4 Expansion plans and funding
- 4.7 Product portfolio & technology benchmarking
- 4.8 Research & development investment analysis
- 4.9 Market concentration & vendor ecosystem
- 4.10 Distribution channel & partner network analysis
- 4.11 Vendor roadmap alignment assessment
- 4.12 Technology integration complexity matrix
- 4.13 Vendor financial stability assessment
Chapter 5 Market Estimates & Forecast, By Component, 2021 - 2034 ($Mn)
- 5.1 Key trends
- 5.2 Solution
- 5.2.1 Identity and access management (IAM)
- 5.2.2 Firewall & network security
- 5.2.3 Data protection & encryption
- 5.2.4 Security information & event management (SIEM)
- 5.2.5 Endpoint security
- 5.2.6 Cloud security solutions
- 5.3 Services
- 5.3.1 Professional services
- 5.3.1.1 System integration
- 5.3.1.2 Training & consulting
- 5.3.1.3 Support & maintenance
- 5.3.2 Managed services
- 5.3.1 Professional services
Chapter 6 Market Estimates & Forecast, By Organization Size, 2021 - 2034 ($Mn)
- 6.1 Key trends
- 6.2 SME
- 6.3 Large enterprises
Chapter 7 Market Estimates & Forecast, By End Use, 2021 - 2034 ($Mn)
- 7.1 Key trends
- 7.2 BFSI
- 7.3 IT & Telecom
- 7.4 Healthcare
- 7.5 Government & defense
- 7.6 Retail & e-commerce
- 7.7 Others
Chapter 8 Market Estimates & Forecast, By Deployment, 2021 - 2034 ($Mn)
- 8.1 Key trends
- 8.2 On-premises
- 8.3 Cloud-based
Chapter 9 Market Estimates & Forecast, By Region, 2021 - 2034 ($Mn)
- 9.1 Key trends
- 9.2 North America
- 9.2.1 US
- 9.2.2 Canada
- 9.3 Europe
- 9.3.1 Germany
- 9.3.2 UK
- 9.3.3 France
- 9.3.4 Italy
- 9.3.5 Spain
- 9.3.6 Nordics
- 9.3.7 Russia
- 9.4 Asia Pacific
- 9.4.1 China
- 9.4.2 India
- 9.4.3 Japan
- 9.4.4 South Korea
- 9.4.5 ANZ
- 9.4.6 Southeast Asia
- 9.5 Latin America
- 9.5.1 Brazil
- 9.5.2 Mexico
- 9.5.3 Argentina
- 9.6 MEA
- 9.6.1 South Africa
- 9.6.2 Saudi Arabia
- 9.6.3 UAE
Chapter 10 Company Profiles
- 10.1 Global companies
- 10.1.1 Amazon Web Services (AWS)
- 10.1.2 Broadcom
- 10.1.3 Check Point Software Technologies
- 10.1.4 Cisco Systems
- 10.1.5 CrowdStrike
- 10.1.6 Fortinet
- 10.1.7 Google
- 10.1.8 Hewlett Packard Enterprise
- 10.1.9 IBM
- 10.1.10 Juniper
- 10.1.11 Microsoft
- 10.1.12 McAfee
- 10.1.13 Palo Alto Networks
- 10.1.14 Trend Micro
- 10.1.15 Continental
- 10.2 Regional companies
- 10.2.1 Okta
- 10.2.2 Ping Identity
- 10.2.3 Qualys
- 10.2.4 Rapid7
- 10.2.5 SentinelOne
- 10.2.6 Splunk
- 10.2.7 Tenable
- 10.2.8 Varonis Systems
- 10.3 Emerging players
- 10.3.1 Axonius
- 10.3.2 Dynatrace
- 10.3.3 Jit Security
- 10.3.4 Lacework
- 10.3.5 Orca Security
- 10.3.6 Snyk
- 10.3.7 Wiz




