PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1851659

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1851659
Application Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030)
The application security market was valued at USD 13.64 billion in 2025 and is expected to reach USD 30.41 billion by 2030, advancing at a 17.39% CAGR.
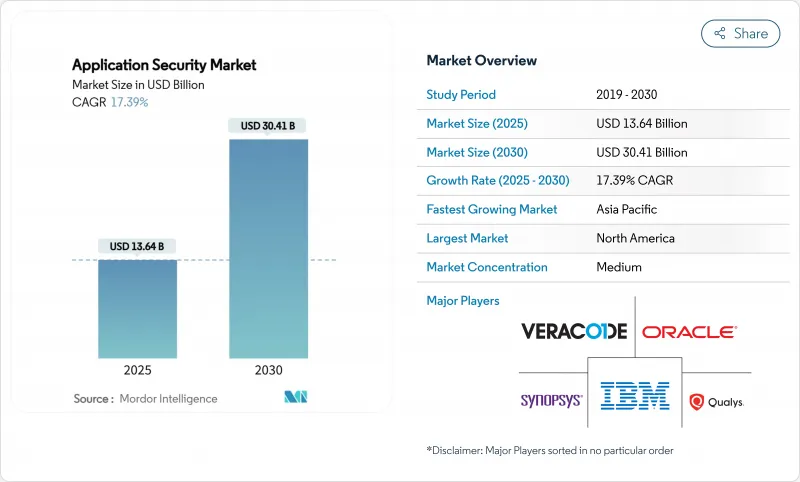
Cloud migration, API-centric software design and expanding regulatory mandates are accelerating adoption across every major industry vertical. Growth is reinforced by a sharp increase in API traffic, the widespread use of AI-generated code and heightened incident disclosure rules that force organizations to strengthen testing earlier in the development life cycle. Large enterprises continue to anchor overall spending, yet managed platforms aimed at small and medium enterprises (SMEs) are opening a sizeable new addressable base for vendors. Technology convergence is reshaping competitive dynamics, with platform providers integrating static, dynamic and runtime protection to curb tool sprawl and improve developer productivity.
Global Application Security Market Trends and Insights
Rising Volume and Sophistication of Web, Mobile and API-Based Attacks
Web application attacks in the Asia-Pacific region surged 73% to 51 billion events in 2024, underscoring how attackers now exploit APIs at scale. Retailers developing more than 1,000 APIs yearly confront an enlarged attack surface that bypasses perimeter controls. Supply-chain breaches climbed 431% between 2021 and 2023, demonstrating a pivot toward dependency exploitation rather than direct code injection. Enterprises are integrating runtime application self-protection with behavioral analytics to act on anomalous traffic patterns rather than static signatures. Manufacturing recorded a 79% API incident rate, confirming that adversaries move faster than most operational technology security programs.
Rapid Adoption of DevSecOps Toolchains
DevSecOps penetration rose from 27% in 2020 to 36% in 2024 as teams embed testing earlier in continuous integration pipelines. Platforms processing billions of findings, such as ArmorCode, apply machine learning to correlate vulnerabilities and prioritize remediation at scale. Despite progress, 78% of enterprises report "shift-left fatigue," aggravated by redundant tools that overwhelm developers with alerts. The most effective programs streamline security tasks inside integrated development environments, treating policies as version-controlled artifacts automatically enforced at commit. This model is extending through AI assistants that suggest fixes inside code editors, thereby reducing context-switch time between development and security portals.
High Total Cost of Ownership and Tool Complexity
Software-as-a-service inflation reached 11.3% in 2024, with some vendors lifting prices by 25%.Forty-two percent of SMEs still lack a structured incident response plan, revealing budget constraints that limit enterprise-grade controls. Organizations deploy overlapping scanners, agents and policy engines that demand scarce integration skills, leading 89% of firms to foresee additional staffing needs despite flat headcounts. Managed platforms such as Contrast One(TM) now bundle expert services with tooling to cut administrative overhead. Consumption-based pricing models are also emerging, enabling smaller businesses to align spending with actual test frequency.
Other drivers and restraints analyzed in the detailed report include:
- Expanding Regulatory Mandates
- Growth in Third-Party SaaS Integrations
- Global Shortage of Secure-Coding Talent
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Solutions retained a 78.5% share in 2024, reflecting enterprise preference for integrated suites. Market leaders combine SAST, DAST, IAST and RASP under one license to limit tool sprawl. Consolidated dashboards reduce context switching and speed decision-making, fixing a common pain point cited by development teams. The service segment, though smaller, outran the broader application security market with a 17.9% CAGR and will continue to benefit from skills gaps.
Demand for managed security accelerates within SMEs that cannot afford full-time specialists. Providers use predictable subscription pricing and outcome-based service-level agreements to attract cost-conscious buyers. For large enterprises, professional services focus on policy mapping, pipeline integration and red-team simulations that validate runtime defenses. Vendors also introduce consumption-tiered offerings, letting customers buy scanning credits rather than perpetual seats, bringing transparency to budgeting for vulnerability management.
Cloud deployment controlled 65.9% of the application security market in 2024 and is forecast to advance at a 19.3% CAGR. DORA and related regulations specify four-hour incident reporting, a timeline difficult to meet without centralized logging and scalable analytics. Cloud-native solutions enable rapid rollout of policy updates and integrate easily with container orchestration systems.
On-premises solutions remain prevalent in defense and public-sector workloads that require data residency. Hybrid patterns are growing as financial firms keep sensitive workloads on private infrastructure while using cloud scanners during development. Cloud vendors invest in hardware-backed attestation and confidential computing to address lingering sovereignty concerns. Competition now centers on alignment with cloud security posture management functions that map misconfigurations across both infrastructure and application layers.
Application Security Market is Segmented by Application Type (Web Application Security, and More), Component (Solutions, Services), Deployment Mode (Cloud, On-Premises), Organization Size (SMEs, Large Enterprises), Security Testing Type (SAST, DAST, and More), End-User Industry (BFSI, Healthcare, Retail and E-Commerce, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America led the application security market with a 28.9% revenue share in 2024, underpinned by strong regulatory pressure and average Fortune 500 security budgets exceeding USD 20 million annually. Enterprises integrate zero-trust architectures that merge identity, network and application controls to support remote and hybrid work. Advancements originate in technology hubs where vendors pilot AI-driven vulnerability correlation workloads, delivering faster mean time to remediation.
Asia-Pacific records the fastest projected 17.5% CAGR through 2030, fueled by digital government programs, rising fintech adoption and a 73% spike in web application attacks that hit 51 billion events in 2024. Governments in Singapore and India release refreshed cyber strategies that map minimum control baselines for critical infrastructure. The region's manufacturing sector, despite lower digital maturity, faces the highest share of API incidents, pushing vendors to localize threat intelligence and language-specific remediation resources.
Europe's momentum hinges on comprehensive statutes such as DORA, the Cyber Resilience Act and GDPR. Financial entities must implement ICT risk management frameworks and deliver four-hour breach notifications from January 2025. Organizations allocate around 9% of IT budgets to information security, yet 89% still anticipate hiring increases to meet these mandates. Hybrid deployment preferences persist because data-sovereignty clauses encourage on-premise processing of sensitive workloads while permitting cloud-based analytics for less critical data.
- IBM
- Synopsys Inc.
- Checkmarx
- Veracode (Thoma Bravo)
- Micro Focus
- Oracle Corporation
- Rapid7
- Qualys
- Palo Alto Networks
- Fortinet
- Trend Micro
- GitLab
- GitHub
- Snyk
- CrowdStrike
- Contrast Security
- WhiteHat Security (NTT)
- Positive Technologies
- SiteLock
- Mend (WhiteSource)
- ArmorCode
- Fasoo
- HCL Software (AppScan)
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Rising volume and sophistication of web-, mobile- and API-based attacks
- 4.2.2 Rapid adoption of DevSecOps toolchains
- 4.2.3 Expanding regulatory mandates (PCI-DSS 4.0, GDPR, DORA, etc.)
- 4.2.4 Growth in third-party/SaaS integrations
- 4.2.5 Mandatory SBOM disclosure post-US Executive Order 14028
- 4.2.6 AI-generated code inflating unknown vulnerabilities
- 4.3 Market Restraints
- 4.3.1 High total cost of ownership and tool complexity
- 4.3.2 Global shortage of secure-coding talent
- 4.3.3 False-positive overload eroding developer trust
- 4.3.4 "Shift-left fatigue" and tool sprawl
- 4.4 Supply-Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Bargaining Power of Suppliers
- 4.7.4 Threat of Substitutes
- 4.7.5 Competitive Rivalry
- 4.8 Assesment of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.2 Services
- 5.2 By Deployment Mode
- 5.2.1 Cloud
- 5.2.2 On-premise
- 5.3 By Organization Size
- 5.3.1 Small and Medium Enterprises
- 5.3.2 Large Enterprises
- 5.4 By Security Testing Type
- 5.4.1 Static Application Security Testing (SAST)
- 5.4.2 Dynamic Application Security Testing (DAST)
- 5.4.3 Interactive Application Security Testing (IAST)
- 5.4.4 Run-time Application Self-Protection (RASP)
- 5.4.5 Software Composition Analysis (SCA)
- 5.5 By End-user Industry
- 5.5.1 BFSI
- 5.5.2 Healthcare
- 5.5.3 Retail and E-commerce
- 5.5.4 Government and Defense
- 5.5.5 IT and Telecom
- 5.5.6 Education
- 5.5.7 Others
- 5.6 By Region
- 5.6.1 North America
- 5.6.1.1 United States
- 5.6.1.2 Canada
- 5.6.1.3 Mexico
- 5.6.2 South America
- 5.6.2.1 Brazil
- 5.6.2.2 Argentina
- 5.6.2.3 Rest of South America
- 5.6.3 Europe
- 5.6.3.1 Germany
- 5.6.3.2 United Kingdom
- 5.6.3.3 France
- 5.6.3.4 Netherlands
- 5.6.3.5 Rest of Europe
- 5.6.4 Asia_Pacific
- 5.6.4.1 China
- 5.6.4.2 Japan
- 5.6.4.3 India
- 5.6.4.4 South Korea
- 5.6.4.5 Rest of Asia-Pacific
- 5.6.5 Middle East and Africa
- 5.6.5.1 Middle East
- 5.6.5.1.1 United Arab Emirates
- 5.6.5.1.2 Saudi Arabia
- 5.6.5.1.3 Turkey
- 5.6.5.1.4 Rest of Middle East
- 5.6.5.2 Africa
- 5.6.5.2.1 Egypt
- 5.6.5.2.2 South Africa
- 5.6.5.2.3 Nigeria
- 5.6.5.2.4 Rest of Africa
- 5.6.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 IBM
- 6.4.2 Synopsys Inc.
- 6.4.3 Checkmarx
- 6.4.4 Veracode (Thoma Bravo)
- 6.4.5 Micro Focus
- 6.4.6 Oracle Corporation
- 6.4.7 Rapid7
- 6.4.8 Qualys
- 6.4.9 Palo Alto Networks
- 6.4.10 Fortinet
- 6.4.11 Trend Micro
- 6.4.12 GitLab
- 6.4.13 GitHub
- 6.4.14 Snyk
- 6.4.15 CrowdStrike
- 6.4.16 Contrast Security
- 6.4.17 WhiteHat Security (NTT)
- 6.4.18 Positive Technologies
- 6.4.19 SiteLock
- 6.4.20 Mend (WhiteSource)
- 6.4.21 ArmorCode
- 6.4.22 Fasoo
- 6.4.23 HCL Software (AppScan)
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment




