PUBLISHER: VDC Research Group, Inc. | PRODUCT CODE: 1618862

PUBLISHER: VDC Research Group, Inc. | PRODUCT CODE: 1618862
The Global Market for Automotive Cybersecurity: Safeguarding the Software-Defined Vehicle
Inside this Report
The automotive industry is undergoing an unprecedented shift toward the software-defined vehicle (SDV) concept that is fundamentally changing the requirements for automotive cybersecurity. This report includes an overview of technologies and trends that influence the automotive cybersecurity market, including telematics and vehicle-to- everything (V2X) communication, payment by car, vehicle charging, infotainment system capabilities, open source architectures, and other industry software initiatives and advancements. As part of VDC's continued efforts to engage with the technology markets we research, this report includes end user insights from VDC's "Voice of the Engineer" survey. Lastly, this report highlights dozens of key automotive cybersecurity vendors that are shaping the market.
INFOGRAPHICS
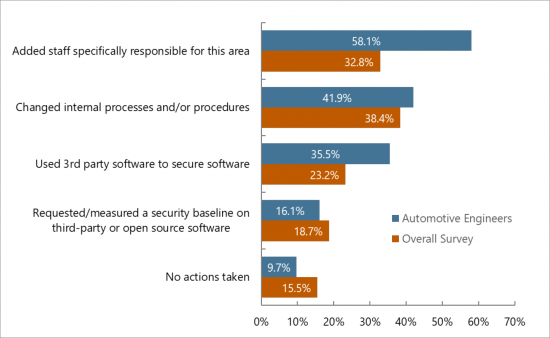
Exhibit 9: Actions Taken by Respondents Organization
in Response to Security Requirements
(Percentage of Respondents, Multiple Responses Permitted)
What Questions are Addressed?
- How has the mass introduction of software and connectivity affected automotive cybersecurity?
- Which segment is growing the fastest - Security software, Security-as-a-service or Professional services?
- What is the future of automotive cybersecurity regulations and what can be gained by understanding the future of regulations?
- Which geographic regions are driving growth in the automotive cybersecurity market through 2028?
- How are IoT engineers and automotive engineers responding to cybersecurity concerns?
- Which firms are shaping the automotive cybersecurity market and how are they doing it?
Who Should Read this Report?
- CEO or other C-level executives
- Corporate development and M&A teams
- Marketing executives
- Business development and sales leaders
- Product development and product strategy leaders
- Channel management and channel strategy leaders
Organizations Listed in this Report:
|
|
Table of Contents
Inside this Report
What Questions are Addressed?
Who Should Read this Report?
Organizations Listed in this Report
Executive Summary
- Key Findings
Introduction
- Software-Defined Vehicles Expose Vulnerabilities
- Where does Cybersecurity Fit in the Transition to the SDV?
- V2X Connectivity
- In-Car Payments
- Vehicle Charging
- Apps and APIs
- The Role of Artificial Intelligence
- Open Source and Open Architecture
- Product Landscape
Global Market Overview
- Automotive Cybersecurity Product Segmentation
- Product Segmentations within the Automotive Cybersecurity Market
Regulations Driving Growth
- WP.29 Regulations 155 and 156
- ISO/SAE 21434
- Regulations in the United States
- China GB 44495-2024 and GB 44496-2024
- India AISC AIS-189 and AIS-190
Regional Analysis
Industry Consortia and Standards Organizations
- ASRG
- AUTO-ISAC
- COVESA
- digital.auto initiative
- Eclipse SDV
- eSync Alliance
- MIPI Alliance
- Uptane
Vendor Landscape
- Vendor Profiles
- BlackBerry QNX
- Block Harbor
- Bosch / ETAS
- Continental / Elektrobit / PlaxidityX
- Green Hills Software
- Integrity Security Services
- Irdeto
- Karamba Security
- Kaspersky
- HARMAN
- Sonatus
- Thales
- VicOne
- Upstream
- Vector
End User Insights
- Industry Adaptation to Security Requirements
- Vendor Landscape Favors Innovation
- Diminishing Influence of Established Tech and System Integrators
- Implementation of Embedded Security Software, Hardware, and FOTA
- The Future of Automotive Technology
About the Authors
About VDC Research
List of Exhibits*
- Exhibit 1 Biggest Obstacle to the Development and Growth of the Connected/Software-Defined Vehicle Industry
- Exhibit 2: Current Concerns About AI-generated Software Code
- Exhibit 3: Sample Table of Vendors Offering Automotive Cybersecurity Solutions
- Exhibit 4: Global Revenue of Automotive Cybersecurity Software and Services
- Exhibit 5: Global Revenue for Automotive Cybersecurity Software and Services by Product Category
- Exhibit 6: Global Revenue for Automotive Cybersecurity and Software, 2023 to 2028, Share by Product Category
- Exhibit 7: Global Revenue for Automotive Cybersecurity Software and Services by Region
- Exhibit 8: Global Revenue of Automotive Cybersecurity Software & Services by Geographic
- Exhibit 9: Actions Taken by Respondents Organization in Response to Security Requirements
- Exhibit 10: Current Major Competition in the Software-defined Space
- Exhibit 11: Use of Embedded Security Software, Hardware, & Firmware-Over-the-Air Updating in Current Automotive Projects vs. Overall IoT Projects
- Exhibit 12: Technologies Automotive Respondent's Organization is Most Interested in and/or Building for Future Customers
*This report also includes access to 416 Exhibits from our 2024 Voice of the Engineer Survey.




