PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1906217

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1906217
Malaysia Cybersecurity - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2026 - 2031)
The Malaysia cybersecurity market is expected to grow from USD 6.15 billion in 2025 to USD 6.59 billion in 2026 and is forecast to reach USD 9.32 billion by 2031 at 7.16% CAGR over 2026-2031.
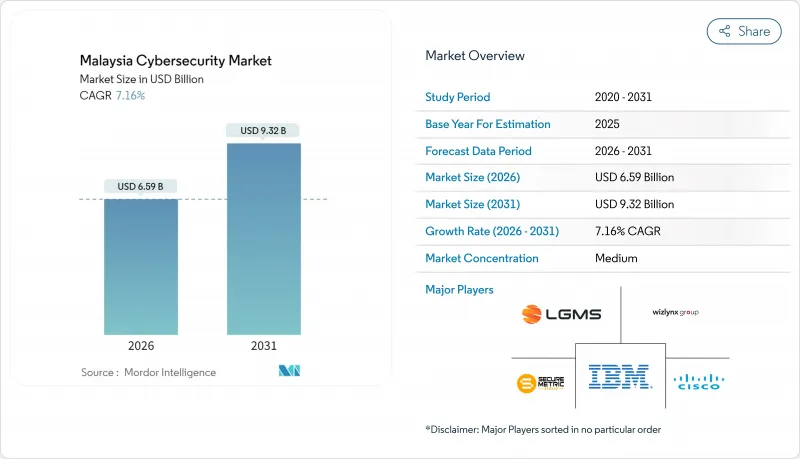
This low-double-digit trajectory positions the Malaysia cybersecurity market among the faster-growing digital-infrastructure segments within the country's wider ICT ecosystem. Cloud-first mandates, strict licensing under the Cyber Security Act 2024, and the monetized cost of data breaches are each propelling sustained demand. Large enterprises are broadening existing controls into zero-trust programs, while small and medium enterprises are starting first-time deployments through subscription services that lower upfront costs. Parallel investments in 5G edge networks, hyperscale data centers, and operational-technology modernization further anchor a long runway for the Malaysia cybersecurity market.
Malaysia Cybersecurity Market Trends and Insights
Rapid Roll-out of Malaysia's Cloud-First Strategy Propelling Public-Sector Cloud Security Spending
Malaysia's accelerated cloud-first strategy is redirecting government spending toward cloud-native defenses such as cloud access security brokers and workload-protection platforms. Ministries now integrate classification, encryption, and continuous monitoring into every application-migration plan, lifting baseline demand for advisory and managed services. Public-sector visibility into early success stories is encouraging financial institutions and telecom carriers to adopt similar architectures, creating a multiplier effect across the Malaysia cybersecurity market. System integrators have redesigned portfolios around shared-responsibility models, bundling consulting, deployment, and managed detection under single contracts. Collectively, these changes translate to a structural uplift in addressable spending rather than a one-time spike.
Cyber Security Act 2024 Licensing and Mandatory NCII Compliance Fuelling Vendor Demand
The Cyber Security Act 2024 enforces mandatory licensing for penetration testing, security-operations, and other core services, while critical-infrastructure operators must observe sector-specific codes of practice. Organizations have responded by elevating compliance to board-level priority and retaining external auditors to align controls with the new legal baseline. Providers that secured early licences gained a measurable sales advantage because enterprises prefer pre-qualified partners to avoid regulatory missteps. The act also formalized incident-reporting timelines, spurring demand for real-time detection tools and threat-intelligence integrations. Together, these shifts embed recurring compliance obligations into IT budgets, sustaining momentum in the Malaysia cybersecurity market size.
Acute Shortage of Senior Security Architects Inflating Project Timelines and Costs
Complex cloud migrations stall because experienced architects remain scarce, extending project timelines by 37% and boosting labor costs by more than one-quarter . The scarcity inflates bids for large transformation contracts, squeezing corporate budgets and delaying key milestones. Organizations counter by outsourcing architecture to MSSPs or importing expertise from regional hubs, but long visa lead times cap near-term relief. Vendor roadmaps now include low-code policy engines and reference architectures that cut design hours, yet hands-on oversight remains indispensable for regulated workloads. Talent constraints therefore act as a persistent drag on the Malaysia cybersecurity market CAGR.
Other drivers and restraints analyzed in the detailed report include:
- Data-Centre Boom in Johor Bahru Elevating Perimeter and OT Security Investments
- 5G Coverage >= 97 % Driving Mobile Core and Edge Security Upgrades
- SME Budget Constraints Owing to Legacy CAPEX-heavy IT Footprints
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Solutions maintained 52.20% share of the Malaysia cybersecurity market in 2025, led by network and cloud-security suites that protect hybrid environments. However, services are forecast to outpace solutions at a 7.42% CAGR through 2031 as enterprises look for always-on expertise. Higher detection accuracy, round-the-clock monitoring, and built-in compliance dashboards position MSSPs as strategic partners rather than tactical suppliers. Pricing models based on monthly active assets lower entry barriers for mid-tier firms. Local providers leverage regulatory familiarity to capture contracts tied to the Cyber Security Act, while global vendors package orchestration platforms that unify alerts across point tools. Convergence of advisory, deployment, and MDR services brings value propositions beyond technology resale, solidifying service-led growth in the Malaysia cybersecurity market.
The solutions portfolio nevertheless remains critical for organizations with strict data-residency rules. Appliance refresh cycles in BFSI and utilities sustain revenue for firewall, intrusion-prevention, and secure-email gateways. New-generation SIEM platforms incorporate behavioral analytics and automation to offset talent scarcity, aligning product innovation with national skills-development goals. Vendors bundle perpetual licenses with cloud-delivered analytics to bridge on-premise controls and SaaS visibility. Co-delivery with local integrators accelerates time to value, reflecting the collaborative nature of the Malaysia cybersecurity market.
On-premise systems accounted for 52.85% of the Malaysia cybersecurity market size in 2025 because legacy workloads and data-sovereignty mandates still dominate in banking and public service. Hardware refreshes in these sectors provide a stable base for appliance vendors. Yet cloud deployments are expanding at an 8.05% CAGR through 2031, outstripping on-premise upgrades. Consumption-based pricing, continuous feature releases, and AI-driven analytics make cloud controls appealing for institutions pursuing digital-first strategies. Shared-responsibility frameworks encourage enterprises to off-load maintenance to specialized providers, supporting long-term adoption in the Malaysia cybersecurity market.
Vendor roadmaps include data-localization nodes within Malaysia to reassure regulated customers. Over time, improvements in sovereign-cloud platforms may erode the remaining resistance, but hardware refreshes tied to industrial-control networks ensure a continuing market for on-premise gear.
The Malaysia Cybersecurity Market Report is Segmented by Offering (Solutions [Application Security, Cloud Security, and More], Services [Professional Services, and More]), Deployment Mode (Cloud, On-Premise), End-User Industry (BFSI, Healthcare, IT and Telecom, Industrial and Defense, Retail and E-Commerce, and More), End-User Enterprise Size (Large Enterprises, Smes). The Market Forecasts are Provided in Terms of Value (USD).
List of Companies Covered in this Report:
- LGMS Berhad
- IBM Corporation
- Cisco Systems Inc.
- Securemetric Bhd
- Wizlynx Group
- Akati Sekurity
- Palo Alto Networks
- Fortinet Inc.
- Check Point Software Tech.
- Trend Micro Inc.
- Kaspersky Lab
- Nexagate Sdn Bhd
- Ishan Tech Sdn Bhd
- Capgemini SE
- Microsoft Corp.
- AVG Technologies (Gen Digital)
- ATandT Cybersecurity
- NTT Data Security
- BAE Systems AI Malaysia
- Darktrace plc
- CrowdStrike Holdings Inc.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Market Definition and Study Assumptions
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Rapid Roll-out of Malaysia's Cloud-First Strategy Propelling Public-Sector Cloud Security Spending
- 4.2.2 Cyber Security Act 2024 Licensing and Mandatory NCII Compliance Fuelling Vendor Demand
- 4.2.3 Data-Centre Boom in Johor Bahru Elevating Perimeter and OT Security Investments
- 4.2.4 5G Coverage >= 97 % Driving Mobile Core and Edge Security Upgrades
- 4.2.5 USD 12.2 bn Economic Losses From Breaches Raising Boardroom Budgets
- 4.2.6 National Goal of 25 000 Cyber Defenders Boosting Consulting and Training Spend
- 4.3 Market Restraints
- 4.3.1 Acute Shortage of Senior Security Architects Inflating Project Timelines and Costs
- 4.3.2 SME Budget Constraints Owing to Legacy CAPEX-heavy IT Footprints
- 4.3.3 Fragmented Cross-border Data-Sovereignty Rules Slowing Cloud Migrations
- 4.3.4 Low Multi-factor-Auth Adoption Outside BFSI Heightening Residual Risk
- 4.4 Value Chain Analysis
- 4.5 Evaluation of Critical Regulatory Framework
- 4.6 Impact Assessment of Key Stakeholders
- 4.7 Technological Outlook
- 4.8 Porter's Five Forces Analysis
- 4.8.1 Bargaining Power of Suppliers
- 4.8.2 Bargaining Power of Consumers
- 4.8.3 Threat of New Entrants
- 4.8.4 Threat of Substitutes
- 4.8.5 Intensity of Competitive Rivalry
- 4.9 Impact of Macro-economic Factors
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Offering
- 5.1.1 Solutions
- 5.1.1.1 Application Security
- 5.1.1.2 Cloud Security
- 5.1.1.3 Data Security
- 5.1.1.4 Identity and Access Management
- 5.1.1.5 Infrastructure Protection
- 5.1.1.6 Integrated Risk Management
- 5.1.1.7 Network Security
- 5.1.1.8 End-point Security
- 5.1.2 Services
- 5.1.2.1 Professional Services
- 5.1.2.2 Managed Services
- 5.1.1 Solutions
- 5.2 By Deployment Mode
- 5.2.1 Cloud
- 5.2.2 On-Premise
- 5.3 By End-user Industry
- 5.3.1 BFSI
- 5.3.2 Healthcare
- 5.3.3 IT and Telecom
- 5.3.4 Industrial and Defense
- 5.3.5 Retail and E-commerce
- 5.3.6 Energy and Utilities
- 5.3.7 Manufacturing
- 5.3.8 Others
- 5.4 By End-user Enterprise Size
- 5.4.1 Large Enterprises
- 5.4.2 Small and Medium Enterprises (SMEs)
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 LGMS Berhad
- 6.4.2 IBM Corporation
- 6.4.3 Cisco Systems Inc.
- 6.4.4 Securemetric Bhd
- 6.4.5 Wizlynx Group
- 6.4.6 Akati Sekurity
- 6.4.7 Palo Alto Networks
- 6.4.8 Fortinet Inc.
- 6.4.9 Check Point Software Tech.
- 6.4.10 Trend Micro Inc.
- 6.4.11 Kaspersky Lab
- 6.4.12 Nexagate Sdn Bhd
- 6.4.13 Ishan Tech Sdn Bhd
- 6.4.14 Capgemini SE
- 6.4.15 Microsoft Corp.
- 6.4.16 AVG Technologies (Gen Digital)
- 6.4.17 ATandT Cybersecurity
- 6.4.18 NTT Data Security
- 6.4.19 BAE Systems AI Malaysia
- 6.4.20 Darktrace plc
- 6.4.21 CrowdStrike Holdings Inc.
7 MARKET OPPORTUNITIES AND FUTURE TRENDS
- 7.1 White-space and Unmet-need Assessment




