PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1937396

PUBLISHER: Mordor Intelligence | PRODUCT CODE: 1937396
Africa Cybersecurity - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2026 - 2031)
The Africa cybersecurity market is expected to grow from USD 0.68 billion in 2025 to USD 0.77 billion in 2026 and is forecast to reach USD 1.44 billion by 2031 at 13.3% CAGR over 2026-2031.
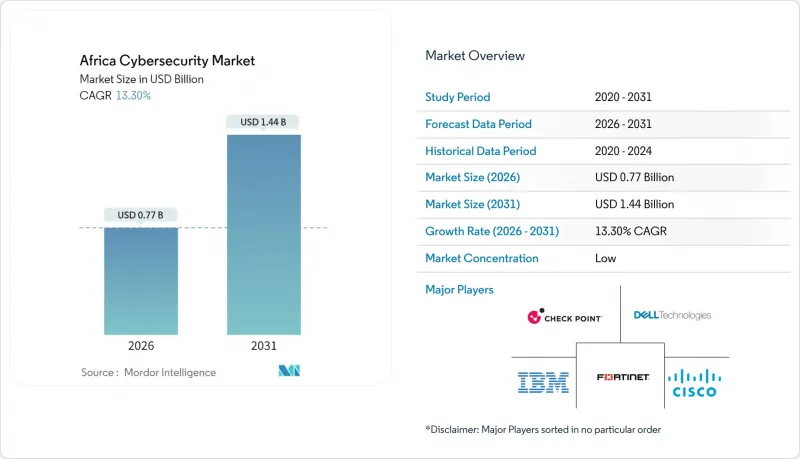
This rapid momentum links directly to the continent's submarine-cable build-out, expanding cloud data-center footprints, and tighter regional data-protection laws. Hyperscaler investments, such as the USD 1 billion Microsoft-G42 digital-ecosystem program in Kenya, move the procurement baseline from point-solutions toward layered, cloud-native security platforms microsoft.com. Enterprises also confront a chronic shortage of certified professionals less than two experts per 100,000 population prompting many to rely on managed security service providers. Regulatory harmonization under acts such as Nigeria's NDPA and South Africa's POPIA is compelling multinational firms to localize data processing and unify governance controls across borders. Meanwhile, mobile-money adoption has heightened fraud exposure, making AI-driven biometric verification and anti-money-laundering analytics indispensable across financial services.
Africa Cybersecurity Market Trends and Insights
Rapid adoption of mobile-money platforms across SSA
Fraud-detection engines uncovered 16% biometric-fraud rates in 2024, quadruple the level at user registration, underscoring how identity-farming rings compromise credentials across SIM swaps and layered laundering chains . East Africa registers rejection rates as high as 27% due to sub-standard ID documentation and weak verification systems. Uganda alone lost USD 3.2 million to mobile-money fraud in 2024, catalyzing a surge in AI-driven anomaly-detection tools and dynamic liveness checks that reposition cybersecurity as a growth enabler for financial inclusion rather than a cost of compliance.
Expansion of national data-protection regulations
Nigeria's 2023 Data Protection Act spurred 92% of surveyed organizations to strengthen security controls within 12 months, while Meta's USD 220 million fine illustrated regulators' willingness to impose material penalties for non-compliance . Kenya's Tier 1 ranking in the Global Cybersecurity Index and the detection of 2.5 billion threats during Q1 2025 reaffirm how early statutory adoption improves national risk posture technext24.com. Multinationals are therefore pivoting to unified, continent-wide governance frameworks and localized data-processing hubs.
Severe shortage of certified cyber-security talent (< 2 pros/100 k pop.)
Nigeria alone needs 30,000 additional experts by 2030, yet premium cloud-security salaries in South Africa already exceed ZAR 786,648 (USD 41,400) for mid-level roles, inflating costs for local firms . Enterprises consequently embrace Security-Operations-Center-as-a-Service models and automation to offset human bottlenecks. Although UNDP and Carnegie Mellon competitions train new cohorts, their combined reach remains below 2,000 professionals annually, leaving a structural deficit that slows solution uptake .
Other drivers and restraints analyzed in the detailed report include:
- World Bank DE4A digital public-infrastructure funding
- Hyperscaler data-center roll-outs driving cloud-native security
- Legacy SS7-based telco infrastructure
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
The Africa cybersecurity market recorded solutions revenue of 67.60% in 2025, yet managed-security offerings are expanding at an 18.2% CAGR, reflecting a decisive shift toward outsourced operations. Enterprises grappling with talent scarcity prefer comprehensive Security-Operations-Center-as-a-Service bundles that combine threat hunting, compliance monitoring, and incident response under single contracts. This outsourcing trend widens margins for regional providers such as Liquid C2, whose AI-infused detection stack benefits from partnerships with hyperscalers. At the same time, the solutions sub-segment faces price pressure from open-source alternatives, prompting vendors to embed value-added analytics and regulatory toolkits.
Professional-services revenue is rising fastest within the broader services mix, as firms navigate multi-jurisdictional privacy laws. Consultants now package "implementation-plus-training" modules, helping clients move from baseline gap assessments to auditable compliance in months rather than years. The Africa cybersecurity market therefore demonstrates a converging spend profile: hardware and software licenses remain foundational, but contractual managed services dominate incremental growth, improving predictability for both buyers and vendors.
On-premise architectures still captured 55.10% of 2025 spend, mirroring legacy data-center footprints, yet cloud adoption is tracking an 14.0% CAGR through 2031. Workload migration toward regional hyperscaler zones creates new perimeter definitions, rendering traditional firewalls insufficient. Financial-services pioneers such as TymeBank showcase how fully cloud-deployed digital banks can satisfy Payment Card Industry Data Security Standard (PCI-DSS) requirements while accelerating feature release cycles. Accordingly, the Africa cybersecurity market size for cloud-delivered controls is forecast to exceed USD 650 million by 2031, as secure access service edge (SASE) frameworks replace patchwork VPN stacks.
Public-sector workloads remain hybrid because data-sovereignty clauses often mandate local storage for citizen records. Local cloud operators in Nigeria and Egypt exploit currency volatility advantages over foreign providers by billing in local denominations, attracting government and telco tenants that require predictable cost structures. Their bundled security controls effectively an extension of cloud hosting channel incremental revenue toward domestic cybersecurity vendors, reinforcing regional ecosystems.
The Africa Cybersecurity Market Report Segments the Industry Into Offering (Solutions and Services), Deployment Mode (On-Premise, and Cloud), End-User Vertical (BFSI, Healthcare, IT and Telecom, Industrial and Defense, Manufacturing, Retail and E-Commerce, Energy and Utilities, and Others), and End-User Enterprise Size (SMEs, and Large Enterprises). The Market Forecasts are Provided in Terms of Value (USD).
List of Companies Covered in this Report:
- Cisco Systems Inc.
- Check Point Software Technologies Ltd.
- Fortinet Inc.
- Palo Alto Networks Inc.
- IBM Corporation
- Dell Technologies (SecureWorks)
- Broadcom Inc. (Symantec)
- Trend Micro Inc.
- Sophos Group plc
- Kaspersky Lab
- Darktrace plc
- CyberArk Software Ltd.
- Dimension Data (NTT Ltd.)
- Liquid Intelligent Technologies (Liquid C2)
- BCX
- Silensec
- ESET
- Palo Alto Networks (Prisma)
- Huawei Technologies Co. Ltd.
- Oracle Corporation
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Rapid Adoption of Mobile-Money Platforms Across SSA
- 4.2.2 Expansion of National Data-Protection Regulations (NDPR, DPA-Kenya, POPIA)
- 4.2.3 World-Bank DE4A Digital Public-Infrastructure Funding
- 4.2.4 2Africa and Equiano Cable Landings Expanding Bandwidth Attack Surface
- 4.2.5 OT Cybersecurity Demand in Gulf-of-Guinea Oil and Gas
- 4.2.6 Hyperscaler Data-Center Roll-outs Driving Cloud-Native Security
- 4.3 Market Restraints
- 4.3.1 Severe Shortage of Certified Cyber-Security Talent ( <2 Pros/100k pop.)
- 4.3.2 Legacy SS7-Based Telco Infrastructure
- 4.3.3 Fragmented Government Procurement and Long Sales Cycles
- 4.3.4 Low Cyber-Insurance Penetration Among SMEs
- 4.4 Evaluation of Critical Regulatory Framework
- 4.5 Value Chain Analysis
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Competitive Rivalry
- 4.8 Key Use Cases and Case Studies
- 4.9 Impact on Macroeconomic Factors of the Market
- 4.10 Investment Analysis
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Offering
- 5.1.1 Solutions
- 5.1.1.1 Application Security
- 5.1.1.2 Cloud Security
- 5.1.1.3 Data Security
- 5.1.1.4 Identity and Access Management
- 5.1.1.5 Infrastructure Protection
- 5.1.1.6 Integrated Risk Management
- 5.1.1.7 Network Security Equipment
- 5.1.1.8 Endpoint Security
- 5.1.1.9 Other Services
- 5.1.2 Services
- 5.1.2.1 Professional Services
- 5.1.2.2 Managed Services
- 5.1.1 Solutions
- 5.2 By Deployment Mode
- 5.2.1 On-Premise
- 5.2.2 Cloud
- 5.3 By End-User Vertical
- 5.3.1 BFSI
- 5.3.2 Healthcare
- 5.3.3 IT and Telecom
- 5.3.4 Industrial and Defense
- 5.3.5 Manufacturing
- 5.3.6 Retail and E-commerce
- 5.3.7 Energy and Utilities
- 5.3.8 Others
- 5.4 By End-User Enterprise Size
- 5.4.1 Small and Medium Enterprises (SMEs)
- 5.4.2 Large Enterprises
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles {(includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)}
- 6.4.1 Cisco Systems Inc.
- 6.4.2 Check Point Software Technologies Ltd.
- 6.4.3 Fortinet Inc.
- 6.4.4 Palo Alto Networks Inc.
- 6.4.5 IBM Corporation
- 6.4.6 Dell Technologies (SecureWorks)
- 6.4.7 Broadcom Inc. (Symantec)
- 6.4.8 Trend Micro Inc.
- 6.4.9 Sophos Group plc
- 6.4.10 Kaspersky Lab
- 6.4.11 Darktrace plc
- 6.4.12 CyberArk Software Ltd.
- 6.4.13 Dimension Data (NTT Ltd.)
- 6.4.14 Liquid Intelligent Technologies (Liquid C2)
- 6.4.15 BCX
- 6.4.16 Silensec
- 6.4.17 ESET
- 6.4.18 Palo Alto Networks (Prisma)
- 6.4.19 Huawei Technologies Co. Ltd.
- 6.4.20 Oracle Corporation
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment




